📚 Mondosol Help Center
Find answers to all your questions about our coaching, courses, and services
Business & Coaching
Master global business success through expert multilingual coaching and the Power Hour Method
1 articleLearning & Education
Master languages faster through cultural immersion and innovative education approaches
11 articlesTravel & Accommodation
Professional travel and accommodation services for educational experiences
16 articlesBooking & Reservations
Streamline your booking and reservation experience with expert guidance
13 articlesGuest Posting
Share your expertise in travel, education, and personal development
6 articlesAffiliate Program
Join our lucrative affiliate program with 50% commissions and €2 sign-up bonus
Coming soonPricing & Payments
Transparent pricing structure for all educational services
1 articlePlatform & Support
Comprehensive support for account management and technical assistance
1 articleAbout Mondosol
Discover our mission to transform global learning through innovative education
Coming soon🔥 Most Popular Questions
Privacy & Security (24)
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Transparency is the foundation of trust. We believe you have the right to know exactly what information we collect, why we collect it, and how we use it. Here’s a complete breakdown of the personal data Mondosol collects.
👤 Account Information
When you create a Mondosol account, we collect:
Required Information
- Full Name: To personalize your experience and address you properly
- Email Address: For account verification, login, and important communications
- Username: Your unique identifier on the platform
- Password: Encrypted and never stored in plain text
Optional Information
- Profile Picture: To personalize your learning profile
- Bio/Description: To share information with the community
- Location/Country: To provide localized content and comply with regional regulations
- Language Preferences: To deliver content in your preferred language(s)
Why We Collect This: To create and manage your account, verify your identity, and provide personalized services.
📚 Learning & Course Data
To track your progress and improve your learning experience:
Course Activity
- Enrollment Dates: When you start each course
- Progress Tracking: Lessons completed, modules finished
- Time Spent: Duration on each lesson and course
- Completion Status: Courses finished and certificates earned
Assessment Data
- Quiz Results: Scores and answers (for feedback and improvement)
- Assignment Submissions: Your work and instructor feedback
- Test Performance: Assessment results and analytics
Learning Preferences
- Course Interests: Topics you’re interested in
- Learning Goals: Your stated objectives
- Skill Levels: Self-reported or assessed proficiency
- Preferred Learning Pace: Fast-track or standard progression
Why We Collect This: To track your progress, provide certificates, personalize recommendations, and improve course content.
💳 Payment & Billing Information
When you make a purchase:
Billing Details
- Billing Name: Name on payment method
- Billing Address: Required for payment processing
- Country/Region: For tax calculations and compliance
- VAT/Tax ID: If applicable for business purchases
Payment Information
- Payment Method Type: Credit card, PayPal, etc.
- Last 4 Digits: For payment method identification
- Transaction History: Purchase dates, amounts, and order details
Important: We never store complete credit card numbers. All payment processing is handled by certified third-party processors (Stripe, PayPal) that are PCI DSS compliant.
Why We Collect This: To process payments, issue invoices, handle refunds, and comply with financial regulations.
💻 Technical & Usage Data
To improve platform performance and user experience:
Device Information
- IP Address: For security, fraud prevention, and geographic content delivery
- Browser Type & Version: To ensure compatibility
- Operating System: To optimize platform performance
- Device Type: Desktop, mobile, or tablet for responsive design
Usage Analytics
- Pages Visited: Which pages you view and how often
- Click Patterns: What buttons and links you interact with
- Session Duration: How long you spend on the platform
- Referral Source: How you found Mondosol (search, social media, direct)
Cookies & Tracking
- Essential Cookies: Required for platform functionality
- Analytics Cookies: To understand user behavior (you can opt-out)
- Marketing Cookies: For personalized advertising (you can opt-out)
Why We Collect This: To improve platform performance, fix bugs, understand user behavior, and enhance user experience.
📧 Communication Data
When you interact with us:
Email Communications
- Support Tickets: Your questions and our responses
- Newsletter Subscriptions: Topics you’re interested in
- Marketing Preferences: What communications you want to receive
- Unsubscribe Requests: Your opt-out preferences
Community Interactions
- Comments & Reviews: Your feedback on courses
- Forum Posts: Community discussions and contributions
- Messages: Direct communications with instructors or support
Why We Collect This: To provide customer support, send requested information, and facilitate community interaction.
🤝 Social Media & Third-Party Data
If you connect social accounts or use third-party services:
- Social Profile Information: Name, profile picture, email (if you sign up via Facebook, Google, LinkedIn)
- Third-Party Integrations: Data from connected apps (with your permission)
- Affiliate Tracking: If you arrive through an affiliate link
Why We Collect This: To simplify account creation, enable social sharing, and track affiliate referrals.
🚫 What We DON’T Collect
We respect your privacy and never collect:
- ❌ Sensitive personal data (race, religion, political views, health information)
- ❌ Data from children under 13 without parental consent
- ❌ Information from your device without permission
- ❌ Data unrelated to our services
- ❌ Information we don’t need for legitimate purposes
📊 How Long We Keep Your Data
We follow data minimization principles:
- Active Accounts: Data retained while your account is active
- Inactive Accounts: Deleted after 3 years of inactivity (with prior notice)
- Legal Requirements: Some data retained longer for legal/tax compliance (typically 7 years)
- Marketing Data: Removed immediately upon unsubscribe
- Right to Erasure: You can request deletion anytime
🔒 Your Data Rights
You have complete control over your data:
- Access: Request a copy of all data we hold
- Correction: Update inaccurate information
- Deletion: Request complete data removal
- Portability: Receive your data in machine-readable format
- Objection: Opt-out of certain data processing
Learn more about your data rights →
🔗 Related Resources
Privacy & Security:
External Resources:
- GDPR Data Collection Guidelines – European standards
- CCPA Consumer Rights – California privacy law
- ICO Data Protection Guide – UK regulations
📞 Questions About Your Data?
We’re committed to transparency. If you have questions about what data we collect:
- Email: eliomondello@mondosol.com
- Subject: “Data Collection Inquiry”
- Response Time: Within 24 hours
We collect only what we need, protect what we collect, and respect your choices. 🔒
Last Updated: October 8, 2025
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Your personal information deserves the highest level of protection. At Mondosol, we implement comprehensive security measures to ensure your data remains safe, private, and secure at all times. In this guide, we’ll walk you through every layer of protection we’ve built to safeguard your information.
🛡️ Our Multi-Layer Security Approach
Rather than relying on just one security measure, we use multiple layers of protection to safeguard your personal information. As a result, your data benefits from redundant security systems that work together seamlessly.
SSL/TLS Encryption
First and foremost, we encrypt all data transmitted between your device and our servers using industry-standard SSL/TLS protocols. Consequently, your information becomes scrambled during transmission, making it unreadable to unauthorized parties.
In practice, this means:
- When you log in, your password travels encrypted through the internet
- Similarly, when you submit course work, the content remains protected
- Additionally, all payment information transfers through secure channels
- Therefore, hackers cannot intercept your data even if they access the network
To verify this protection, always look for the padlock icon in your browser’s address bar when using Mondosol. Furthermore, you can click the padlock to view our security certificate details.
Secure Server Infrastructure
Beyond encryption in transit, we also protect your data at rest. Specifically, we store your personal data on secure servers with restricted physical and digital access.
To accomplish this, we implement several protective measures:
- State-of-the-art firewalls protect against unauthorized intrusion attempts
- In addition, our 24/7 server monitoring detects and responds to potential threats in real-time
- Moreover, we maintain physical security at our data centers with biometric access controls
- As an extra precaution, we conduct regular security perimeter assessments
As a result of these measures, your data remains protected even when you’re not actively using the platform.
Data Encryption at Rest
Not only do we encrypt data during transmission, but also when we store it on our servers. In other words, your sensitive information stays encrypted whether it’s moving or sitting in our database.
To enhance this protection further, we implement additional safeguards:
- First, we manage encryption keys separately from the data itself
- Second, we rotate encryption keys regularly to minimize risk
- Third, we require multi-factor authentication for all system access
- Finally, we maintain encrypted backups in geographically separate locations
Therefore, even in the unlikely event of a server breach, your data remains unreadable without the encryption keys.
🔍 Regular Security Audits & Testing
Rather than waiting for problems to occur, we proactively identify and address vulnerabilities through comprehensive testing programs.
Quarterly Security Assessments
Every three months, independent security experts thoroughly review our systems. During these assessments, they:
- First, examine our infrastructure for potential weaknesses
- Then, test our security protocols against current threat models
- Subsequently, provide detailed recommendations for improvements
- Finally, verify that we’ve implemented previous recommendations
As a result, we stay ahead of emerging security threats and maintain industry-leading protection standards.
Penetration Testing
In addition to audits, we conduct regular penetration testing. Essentially, this means we hire ethical hackers to attempt breaking into our systems. Through this process, we:
- Initially, simulate real-world attack scenarios
- Next, identify vulnerabilities before malicious actors can exploit them
- Then, patch any discovered weaknesses immediately
- Ultimately, strengthen our defenses based on test results
Consequently, our security improves continuously through controlled testing.
Vulnerability Scanning
Beyond manual testing, automated tools continuously monitor for security gaps. Specifically, these systems:
- Constantly scan for known vulnerabilities in our software
- Immediately alert our security team when they detect potential issues
- Subsequently, trigger automatic patching for critical vulnerabilities
- Finally, generate reports for our security review process
Therefore, we can respond to new threats within hours rather than days or weeks.
Code Reviews
Before deploying any updates, our team conducts security-focused code reviews. During this process, we:
- First, examine all new code for security vulnerabilities
- Then, verify compliance with security best practices
- Additionally, test for common attack vectors like SQL injection
- Finally, require approval from multiple security team members
As a result, we prevent security issues from reaching our production environment.
📊 Data Minimization Principle
Unlike many platforms that collect excessive information, we only collect what we truly need. In fact, this principle guides every data collection decision we make.
Purpose Limitation
Specifically, we collect data only for specific, legitimate purposes. For example:
- When you create an account, we collect your email for login and communication
- Similarly, when you enroll in a course, we track your progress for certification
- However, we never collect data “just in case” we might need it later
- Instead, every data point serves a clear, documented purpose
Therefore, we minimize the amount of personal information at risk.
Storage Limitation
Furthermore, we retain information only as long as necessary. In practice, this means:
- Active account data remains available while you use our services
- However, after three years of inactivity, we send deletion notices
- Subsequently, we remove inactive account data unless you respond
- Additionally, we delete temporary data like session tokens immediately after use
As a result, we don’t accumulate unnecessary personal information over time.
Regular Data Purging
In addition to automated deletion, we conduct regular data purging reviews. During these reviews, we:
- First, identify outdated or unnecessary information
- Then, verify that legal retention requirements don’t apply
- Next, securely delete the identified data using military-grade methods
- Finally, document the deletion for compliance purposes
Consequently, your data footprint remains minimal and manageable.
No Excessive Collection
Most importantly, we never ask for information we don’t need. For instance:
- We don’t request your social security number or national ID
- Similarly, we don’t collect sensitive data about race, religion, or health
- Instead, we limit collection to essential account and learning information
- Therefore, you share only what’s necessary for your educational experience
As a result, you maintain greater privacy and control over your personal information.
👥 Strict Access Controls
Not everyone can access your data. In fact, we implement rigorous access controls to ensure only authorized personnel can view your information.
Role-Based Access
First and foremost, team members access only the data necessary for their specific role. For example:
- Customer support can view account details but not payment information
- Meanwhile, instructors see only their students’ course progress
- Similarly, developers access anonymized test data, not production information
- In contrast, only senior security personnel can access full system logs
Therefore, we minimize the number of people who can view your complete profile.
Authentication Protocols
Beyond role restrictions, we implement multi-factor authentication for all system access. Specifically, this means:
- First, employees must enter their password
- Then, they must provide a second factor (authenticator app or hardware token)
- Additionally, they must access systems from approved devices only
- Furthermore, suspicious login attempts trigger immediate security reviews
As a result, unauthorized individuals cannot access our systems even if they steal a password.
Activity Logging
To ensure accountability, we log and monitor all data access. In practice, this means:
- Every time someone views your data, we record who, when, and why
- Subsequently, security systems analyze these logs for unusual patterns
- If suspicious activity occurs, automated alerts notify our security team immediately
- Finally, we retain these logs for audit and compliance purposes
Consequently, we can detect and investigate any unauthorized access attempts.
Background Checks
Before hiring, all employees undergo comprehensive security clearance checks. This process includes:
- First, criminal background verification
- Then, employment history validation
- Additionally, reference checks from previous employers
- Finally, security training and confidentiality agreement signing
Therefore, we ensure that only trustworthy individuals handle your data.
Confidentiality Agreements
In addition to background checks, legal obligations ensure we protect your privacy. Specifically:
- All employees sign comprehensive confidentiality agreements
- These agreements legally bind them to protect user data
- Furthermore, violations result in immediate termination and legal action
- Moreover, these obligations continue even after employment ends
As a result, your data remains protected by both technical and legal safeguards.
💾 Secure Backup Systems
To protect against data loss, we maintain robust backup systems. However, these backups receive the same security protection as your live data.
Encrypted Backups
First and foremost, we fully encrypt all backups using the same standards as production data. This means:
- Even if someone steals backup media, they cannot read the data
- Additionally, we use separate encryption keys for backups and production
- Furthermore, we rotate backup encryption keys on a regular schedule
- Therefore, your historical data remains as secure as your current information
Geographic Redundancy
Beyond encryption, we store backups in multiple secure locations. Specifically:
- Primary backups reside in our main data center
- Secondary backups exist in a geographically separate facility
- Additionally, we maintain offline backups for disaster recovery
- Moreover, all backup locations meet the same security standards
As a result, your data survives even catastrophic events like natural disasters.
Regular Testing
Unlike many organizations, we don’t just create backups—we test them. In fact, we test backup restoration procedures monthly to verify effectiveness. During these tests, we:
- First, select random backup files for restoration
- Then, restore them to a test environment
- Next, verify data integrity and completeness
- Finally, document any issues and implement improvements
Consequently, we know our backups will work when we need them.
Disaster Recovery Plan
In addition to backups, we maintain a comprehensive disaster recovery plan. This plan ensures:
- First, we can restore services within hours of any incident
- Second, your data remains accessible even during emergencies
- Third, we maintain business continuity during disasters
- Finally, we communicate clearly with users during any service interruptions
Therefore, you can trust that your learning progress and data remain safe.
🔐 Payment Security
Because financial information requires special protection, we implement additional security measures for all payment processing.
PCI DSS Compliance
First and foremost, we follow Payment Card Industry Data Security Standards (PCI DSS). In practice, this means:
- We undergo annual security assessments by certified auditors
- Additionally, we maintain network segmentation to isolate payment systems
- Furthermore, we implement strict access controls for payment data
- Moreover, we conduct quarterly network vulnerability scans
As a result, your payment information receives bank-level security protection.
Third-Party Processors
Rather than handling payments directly, we process all transactions through certified secure providers like Stripe and PayPal. This approach offers several advantages:
- First, these processors specialize in payment security
- Second, they maintain PCI DSS Level 1 certification (the highest standard)
- Additionally, they handle fraud detection and prevention
- Furthermore, they assume liability for payment security
Therefore, your financial information benefits from industry-leading protection.
No Card Storage
Most importantly, we never store complete credit card numbers. Instead:
- Payment processors store your card details securely
- We receive only the last four digits for display purposes
- Additionally, we never see or store CVV security codes
- Furthermore, we cannot access your full payment information
Consequently, even if someone breaches our systems, they cannot steal your credit card data.
Tokenization
In addition to not storing cards, we replace payment information with secure tokens. Essentially, this means:
- When you save a payment method, we receive a random token
- This token references your card without containing actual card data
- Subsequently, we use this token for future transactions
- However, the token is useless to anyone except our payment processor
Therefore, your payment information remains protected through multiple security layers.
📱 Additional Security Measures
Beyond the core protections, we implement several additional security measures to safeguard your data.
GDPR Compliance
First, we maintain full compliance with EU General Data Protection Regulation (GDPR). This means:
- We respect all your data rights (access, deletion, portability)
- Additionally, we obtain clear consent before collecting data
- Furthermore, we process data lawfully and transparently
- Moreover, we report any breaches within 72 hours
Therefore, you benefit from Europe’s strongest privacy protections regardless of your location.
Privacy by Design
Rather than adding security later, we build it into every feature from the ground up. In practice, this means:
- When designing new features, we consider privacy implications first
- Subsequently, we implement privacy-protective defaults
- Additionally, we minimize data collection in all new features
- Finally, we conduct privacy impact assessments before launch
As a result, security and privacy are fundamental to our platform, not afterthoughts.
Incident Response Plan
In case of security incidents, we maintain rapid response procedures. Our plan includes:
- Immediate containment protocols to limit damage
- Subsequently, forensic investigation to understand the scope
- Then, user notification within required timeframes
- Finally, remediation and prevention of future incidents
Therefore, we can respond quickly and effectively to any security event.
User Education
Because security is a partnership, we provide resources to help you protect your own account. These resources include:
- Security best practices guides and tutorials
- Regular updates about emerging threats
- Additionally, tips for creating strong passwords
- Furthermore, guidance on recognizing phishing attempts
Consequently, you can take an active role in protecting your account.
Regular Updates
Finally, we keep our systems and software current with security patches. Specifically:
- We monitor security bulletins from all our software vendors
- Then, we test patches in our development environment
- Subsequently, we deploy critical patches within 24-48 hours
- Additionally, we conduct regular system updates during maintenance windows
As a result, we protect against newly discovered vulnerabilities quickly.
🚨 What We Do in Case of a Breach
In the unlikely event of a security breach, we take immediate and comprehensive action to protect you.
Immediate Containment
First and foremost, we isolate the threat within minutes of detection. This involves:
- Immediately, our automated systems detect unusual activity
- Then, they trigger containment protocols automatically
- Subsequently, our security team assesses the situation
- Finally, we implement additional manual containment measures
Therefore, we minimize the potential impact of any security incident.
Investigation
Once contained, we conduct thorough forensic analysis to understand the scope. During this investigation, we:
- First, determine what data the attackers accessed
- Then, identify how they gained access
- Next, assess the extent of the compromise
- Finally, document all findings for regulatory reporting
Consequently, we understand exactly what happened and can respond appropriately.
User Notification
In accordance with GDPR, we notify affected users within 72 hours. Our notification includes:
- First, a clear explanation of what happened
- Then, details about what data was affected
- Additionally, steps we’re taking to address the issue
- Furthermore, recommendations for protecting yourself
- Finally, contact information for questions and support
Therefore, you receive timely and transparent communication about any incidents affecting your data.
Remediation
After notification, we patch vulnerabilities immediately. This process includes:
- First, fixing the specific vulnerability that was exploited
- Then, conducting a comprehensive security review
- Subsequently, implementing additional protective measures
- Finally, retesting to ensure the issue is fully resolved
As a result, we prevent similar incidents from occurring in the future.
Transparency
Throughout the process, we ensure full disclosure of what happened and our response. Specifically, we:
- Publish detailed incident reports on our website
- Additionally, update users regularly as we learn more
- Furthermore, share lessons learned with the security community
- Moreover, implement recommended improvements from external experts
Therefore, we maintain accountability and continuously improve our security posture.
🔗 Related Resources
To learn more about your security and privacy, explore these helpful resources:
Last Updated: October 8, 2025
Leave a Reply
Discover immediate steps to take if you suspect unauthorized access to your Mondosol account. Learn how to secure your account, detect suspicious activity, and prevent future security breaches
DiscovDiscovering unauthorized access to your Mondosol account can be stressful. If you suspect someone has accessed your account without permission, follow these critical steps to protect your unauthorized account access and secure your personal information immediately.
🔴 Immediate Steps for Unauthorized Account Access
1. Change Your Password for Account Security
- Quickly log into your Mondosol account security settings
- Create a strong, unique password to prevent unauthorized access
- Use a combination of letters, numbers, and symbols

2. Detect and Remove Unauthorized Sessions
- Go to Settings → Security
- Review login history
- Click Sign Out Everywhere to block unauthorized access
- Check for suspicious login locations or devices
🕵️ Identifying Unauthorized Account Access
Signs of Potential Security Breach
- Unfamiliar login locations
- Unexpected account changes
- Unauthorized purchases
- Suspicious email notifications
🛡️ Comprehensive Account Protection Strategies
Enable Two-Factor Authentication
- Set up 2FA
- Choose between authenticator app or SMS
- Add an extra layer of unauthorized access prevention

Monitor Account Activity
- Regularly check account activity logs
- Set up security alerts
- Review connected applications
📞 Get Immediate Security Support
Urgent Unauthorized Access Concerns:
- Email: security@mondosol.com
- Emergency Response: Within 24 hours
- Provide detailed information about suspected unauthorized access
Quick action protects your account and personal data from unauthorized access. 🔐
📞 Professional Security Support
Need Expert Assistance?
- Contact Cybersecurity Experts:
- External Security Verification:
🔗 Related Security Resources
Leave a Reply
Discover how Mondosol protects your learning data with encryption, access controls, and privacy-focused practices. Learn about your rights to access, correct, and delete your educational records while maintaining complete privacy.
Your learning journey is personal and private. At Mondosol, we understand that your course progress, quiz results, and educational achievements deserve the highest level of protection. In this comprehensive guide, we’ll explain exactly how we safeguard your learning data and ensure your educational privacy.
🔒 Understanding Your Learning Data
Before diving into protection measures, let’s clarify what learning data includes and why protecting it matters.
What Constitutes Learning Data?
Your learning data encompasses all information related to your educational activities on Mondosol:
Course Activity Information:
- Enrollment dates for each course you join
- Progress tracking showing completed lessons and modules
- Time spent on each lesson and course section
- Completion status indicating finished courses
- Certificates earned upon course completion
Assessment and Performance Data:
- Quiz results including scores and answers
- Assignment submissions and instructor feedback
- Test performance across all assessments
- Practice exercise results and attempts
- Skill assessments measuring your proficiency levels
Learning Preferences and Behavior:
- Course interests and topics you explore
- Learning pace preferences (fast-track or standard)
- Study patterns showing when you’re most active
- Content interactions like bookmarks and notes
- Video playback preferences and watch history
According to educational privacy experts at the Student Privacy Compass, protecting learning data is essential for maintaining trust and encouraging honest educational engagement.
🛡️ Multi-Layer Learning Data Protection
Rather than relying on single security measures, we implement multiple protection layers specifically designed for learning data security.
Encryption for Learning Data
First and foremost, we encrypt all your learning data both in transit and at rest:
Data in Transit:
- When you submit quiz answers, we encrypt them using SSL/TLS protocols
- Similarly, course progress updates travel through secure, encrypted channels
- Additionally, all API communications use industry-standard encryption
- Therefore, no one can intercept your learning data during transmission
Data at Rest:
- We encrypt all stored learning data using AES-256 encryption
- Furthermore, we maintain separate encryption keys for different data types
- Moreover, we rotate encryption keys regularly to enhance security
- As a result, your learning records remain unreadable without proper authorization
Research from the National Institute of Standards and Technology emphasizes that encryption is fundamental to protecting sensitive educational records.
Access Control for Educational Records
Not everyone at Mondosol can view your learning data. Instead, we implement strict role-based access controls:
Who Can Access Your Learning Data:
- You: Full access to all your learning records and progress
- Your instructors: Limited access to your performance in their specific courses only
- Support staff: Restricted access only when assisting with technical issues
- System administrators: Encrypted, logged access for maintenance purposes only
Who Cannot Access Your Learning Data:
- ❌ Other students or community members
- ❌ Marketing teams or sales personnel
- ❌ Third-party advertisers or partners
- ❌ Anyone outside Mondosol without your explicit consent
Additionally, we log every instance when someone accesses your learning data, creating a complete audit trail for accountability.
Secure Database Infrastructure
Beyond encryption and access controls, we protect your learning data through robust infrastructure:
Database Security Measures:
- Dedicated servers specifically for educational records
- Firewall protection preventing unauthorized network access
- Regular security audits by independent cybersecurity experts
- Automated backups stored in geographically separate locations
- Disaster recovery systems ensuring data availability
According to database security standards from OWASP, layered security approaches provide the strongest protection for sensitive information.
📊 Learning Data Privacy Practices
Beyond technical security, we implement privacy-focused practices that respect your educational journey.
Data Minimization for Learning Records
We only collect learning data that directly supports your educational experience:
What We Collect and Why:
- Course progress: To show you where you left off and track completion
- Quiz scores: To provide feedback and generate certificates
- Time spent: To optimize course pacing and content length
- Learning preferences: To personalize recommendations
What We Don’t Collect:
- ❌ Unnecessary personal information unrelated to learning
- ❌ Behavioral data for advertising purposes
- ❌ Information about other websites you visit
- ❌ Data from your device beyond what’s needed for platform functionality
Therefore, we minimize your data footprint while maximizing your learning experience.
Anonymized Analytics for Course Improvement
When we analyze learning data to improve courses, we use anonymization techniques:
How We Anonymize Data:
- Remove all personally identifiable information
- Aggregate data across multiple students
- Use statistical methods that prevent re-identification
- Ensure individual students cannot be identified from reports
For example, we might analyze:
- “75% of students complete Module 3 in under 2 hours” ✅
- But never: “John Smith spent 3 hours on Module 3” ❌
Research from the Future of Privacy Forum explains how anonymization protects student privacy while enabling educational improvements.
Instructor Access Limitations
Even your course instructors have limited access to your learning data:
What Instructors Can See:
- ✅ Your progress in their specific course only
- ✅ Your quiz and assignment submissions for grading
- ✅ Your participation in course discussions
- ✅ Your completion status and certificates earned
What Instructors Cannot See:
- ❌ Your activity in other instructors’ courses
- ❌ Your personal contact information (unless you share it)
- ❌ Your payment or billing information
- ❌ Your overall account activity across Mondosol
Furthermore, instructors must agree to strict confidentiality terms before accessing any student data.

🎓 FERPA and Educational Privacy Compliance
As an educational platform, we align our practices with educational privacy regulations, particularly FERPA principles.
FERPA-Aligned Practices
Although FERPA technically applies to U.S. educational institutions receiving federal funding, we adopt its best practices:
FERPA Principles We Follow:
- Student consent: We obtain your permission before sharing learning data
- Limited disclosure: We don’t share educational records without authorization
- Access rights: You can review and request corrections to your learning data
- Security safeguards: We protect educational records from unauthorized access
Learn more about educational privacy rights from the U.S. Department of Education.
International Educational Privacy Standards
Beyond U.S. standards, we comply with international educational privacy requirements:
GDPR Compliance for Learning Data:
- Lawful basis: We process learning data based on contract performance
- Purpose limitation: Data used only for educational purposes
- Data minimization: Collect only necessary learning information
- Storage limitation: Retain data only as long as needed
According to the European Data Protection Board, educational data requires special protection under GDPR.
🔐 Your Control Over Learning Data
You maintain complete control over your learning data throughout your educational journey.
Accessing Your Learning Data
At any time, you can request a complete copy of your learning data:
How to Request Your Learning Data:
- Email eliomondello@mondosol.com
- Subject line: “Learning Data Access Request”
- Include your account email and full name
- Receive your data within 30 days in a readable format
Your data export includes:
- Complete course enrollment history
- All quiz and assessment results
- Certificates and completion records
- Learning preferences and settings
- Progress tracking across all courses
Correcting Learning Data Errors
If you discover inaccuracies in your learning records, you can request corrections:
Common Corrections:
- Quiz scores recorded incorrectly due to technical issues
- Completion status not updating properly
- Certificate information containing errors
- Progress tracking showing incorrect data
To request corrections:
- Contact your course instructor for course-specific issues
- Email support at eliomondello@mondosol.com for technical problems
- Provide specific details about the error
- Receive confirmation once we’ve made corrections
Deleting Your Learning Data
You have the right to request deletion of your learning data:
What Happens When You Delete:
- We remove all your course progress and quiz results
- We delete your certificates and completion records
- We erase your learning preferences and history
- However, we may retain anonymized data for analytics
Important considerations:
- Deletion is permanent and cannot be undone
- You’ll lose all progress and certificates
- You may need to restart courses from the beginning
- Some data may be retained for legal compliance (typically 7 years)
To request deletion:
- Email eliomondello@mondosol.com
- Subject: “Learning Data Deletion Request”
- We’ll process your request within 30 days

Alt text: Student control over learning data including access, correction, and deletion rights
🚫 What We Never Do With Learning Data
To maintain your trust, we make these absolute commitments about your learning data:
We Never Sell Your Learning Data
Unlike some educational platforms, we never sell your learning data to third parties:
- ❌ No data brokers: We don’t sell to data aggregation companies
- ❌ No advertisers: We don’t share learning data for targeted advertising
- ❌ No marketing lists: We don’t sell your information to marketers
- ❌ No third-party analytics: We don’t share identifiable data with external analytics companies
According to a report by the Electronic Frontier Foundation, selling student data undermines educational trust and privacy.
We Never Use Learning Data for Discrimination
Your learning data will never be used against you:
- ❌ Employment decisions: We don’t share data with potential employers without your consent
- ❌ Credit decisions: Learning performance doesn’t affect credit ratings
- ❌ Insurance: Your course activity won’t impact insurance premiums
- ❌ Admissions: We don’t share data with educational institutions without permission
We Never Share Learning Data Publicly
Your educational journey remains private:
- ❌ No public leaderboards: We don’t display your performance publicly without consent
- ❌ No social sharing: We don’t automatically post your progress to social media
- ❌ No public profiles: Your learning data isn’t visible in search engines
- ❌ No community exposure: Other students can’t see your quiz scores or progress
However, you can choose to share your achievements:
- ✅ Opt-in sharing: You control what you share and where
- ✅ Certificate sharing: You can display certificates on LinkedIn or portfolios
- ✅ Achievement badges: You decide whether to show accomplishments publicly
🔗 Related Privacy and Security Resources
Learn more about how we protect your information across Mondosol:
Internal Privacy Resources:
External Educational Privacy Resources:
- FERPA Guidelines – U.S. educational privacy law
- Student Privacy Compass – Educational privacy resources
- Future of Privacy Forum – Student privacy advocacy
- Common Sense Privacy Program – Privacy evaluation tools
💡 Best Practices for Protecting Your Learning Data
While we implement robust protections, you can take additional steps to safeguard your learning data:
Secure Your Account
Your account security directly impacts your learning data protection:
- Use a strong, unique password for your Mondosol account
- Enable two-factor authentication for extra security
- Never share your login credentials with others
- Log out from shared or public computers
- Review account activity regularly for suspicious behavior
Be Cautious About Sharing
Think carefully before sharing your learning achievements:
- Consider who can see your shared certificates or badges
- Review privacy settings on social media before posting
- Understand that shared information may be permanent
- Avoid sharing sensitive quiz results or grades publicly
Monitor Your Learning Data
Regularly review your learning records for accuracy:
- Check your progress tracking monthly
- Verify quiz scores and completion records
- Report any discrepancies immediately
- Request corrections for any errors you find
📞 Questions About Learning Data Protection?
If you have specific concerns about how we protect your learning data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Learning Data Privacy Inquiry”
- Response Time: Within 24-48 hours
For urgent privacy concerns:
- Mark your email as “URGENT”
- Include specific details about your concern
- Expect priority response within 4-8 hours
Your educational privacy is our priority. We’re committed to protecting your learning data with the same care we’d want for our own educational records. 📚🔒
Last Updated: October 8, 2025
Leave a Reply
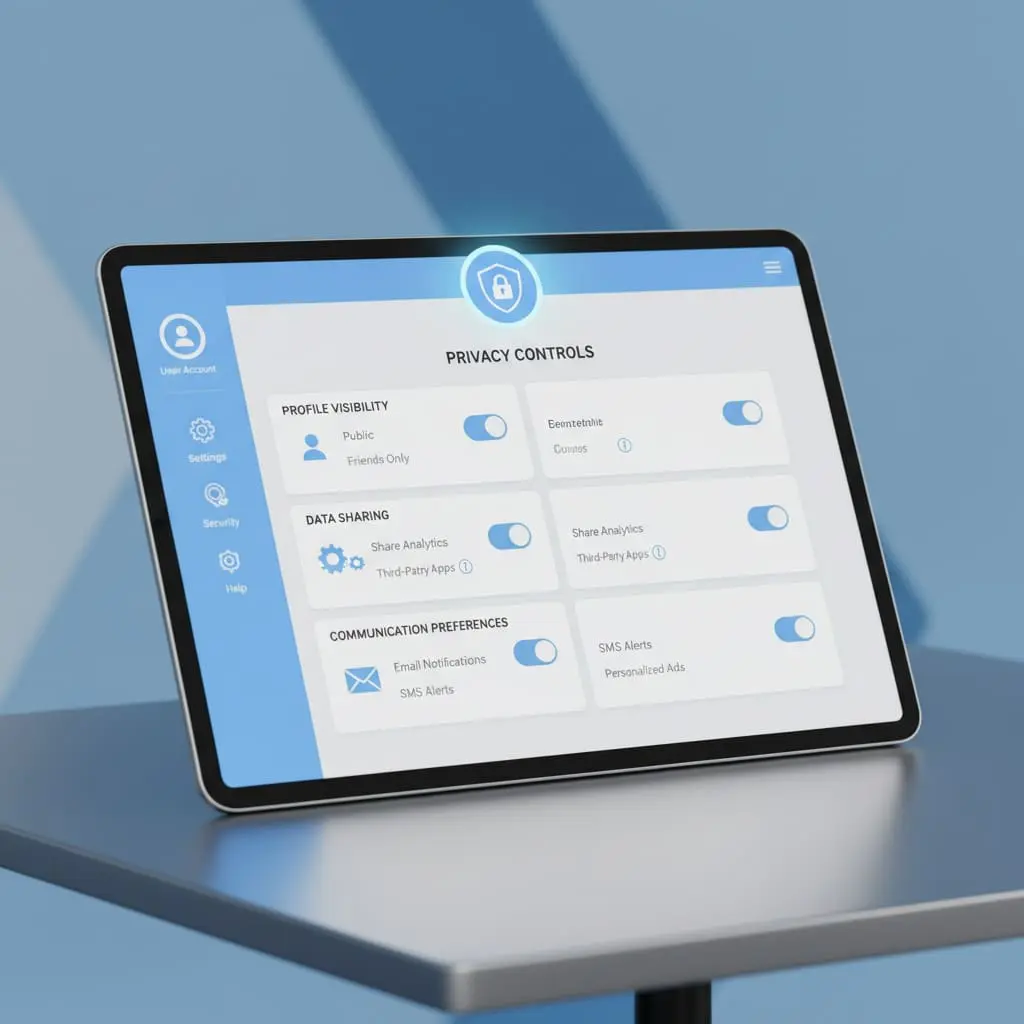
Comprehensive guide to managing your Mondosol privacy settings. Control profile visibility, data sharing, communication preferences, and protect your personal information with granular privacy controls.
Your privacy is in your hands at Mondosol. This comprehensive guide will walk you through every step of managing and customizing your privacy settings to ensure you have complete control over your personal information.
🔒 Privacy Settings Overview
Privacy management is more than just a few toggles—it’s about giving you total control over your digital experience. At Mondosol, we provide granular, easy-to-use privacy controls across multiple dimensions of your account.

Key Privacy Control Areas
You can manage privacy settings in these critical areas:
- Profile Visibility
- Data Sharing Preferences
- Communication Permissions
- Third-Party Integrations
- Content Visibility
- Activity Tracking
🛠️ Accessing Your Privacy Dashboard
To manage your privacy settings, follow these step-by-step instructions:
- Log into your Mondosol account
- Navigate to Settings → Privacy Controls
- Review each section carefully
- Make selections that feel comfortable for you
Pro Tip: Learn more about account security before adjusting settings.
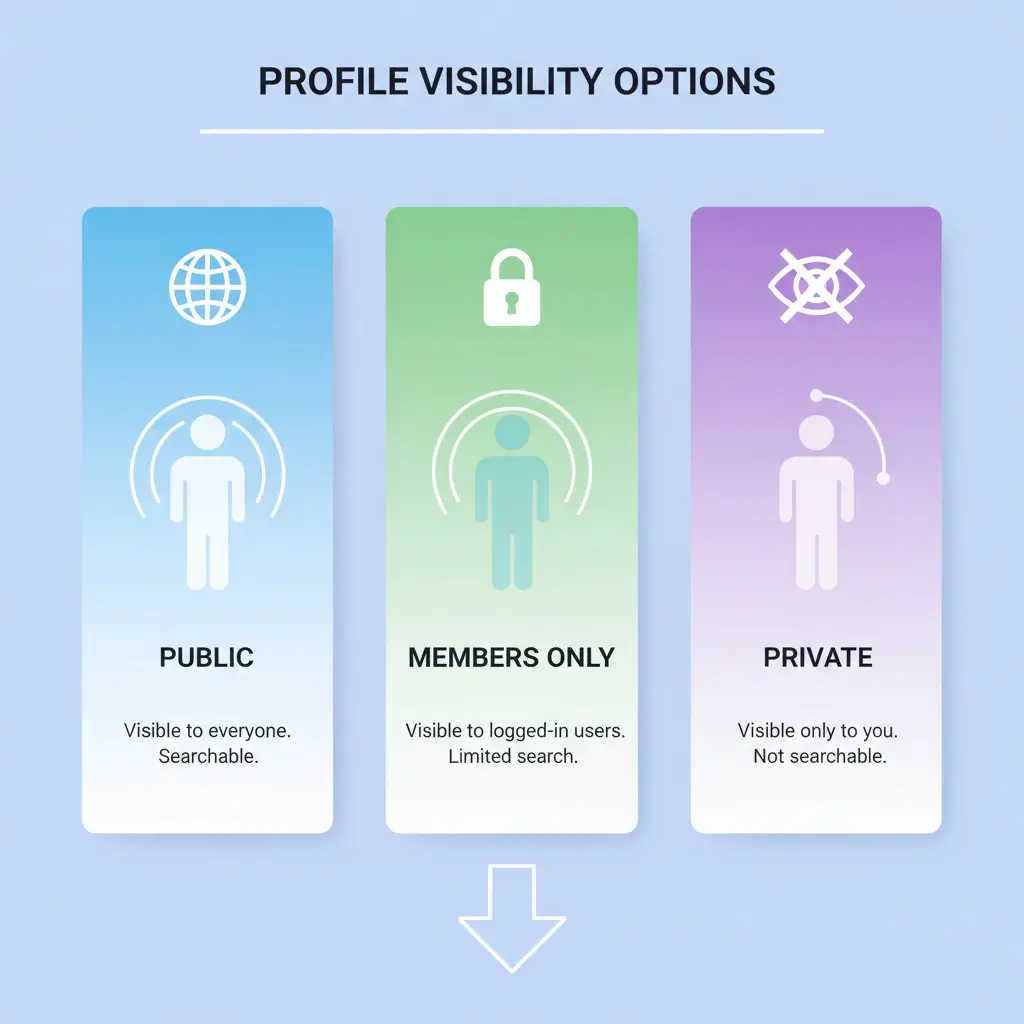
Profile Visibility Options
Control who sees your personal information:
Visibility Levels:
- Public: Anyone can view your profile
- Mondosol Members Only: Visible to registered users
- Private: Completely hidden from other users
- Custom: Create granular visibility rules

Alt text: Multiple privacy levels for controlling profile information visibility
📊 Data Sharing Preferences
Decide exactly how your data is used:
Analytics and Improvement Programs
Choose your level of data contribution:
- Full Participation: Help improve Mondosol’s services
- Limited Sharing: Anonymized data only
- No Participation: Opt-out of all data collection
According to Electronic Frontier Foundation, informed consent is crucial in data sharing.
Third-Party Integration Controls
Manage connections with external services:
Review Connected Apps:
- View all connected applications
- Revoke access for unused or suspicious integrations
- Control what information each app can access
🔔 Communication Permissions
Take control of how and when we communicate:
Email Notification Settings
Customize your communication preferences:
Notification Types:
- Course Updates
- Marketing Communications
- Security Alerts
- Community Notifications
- Promotional Offers
Each category can be individually enabled or disabled.
🌐 International Privacy Compliance
We adhere to global privacy standards:
GDPR and CCPA Compliance
Your rights are protected by:
- Right to access your data
- Right to deletion
- Right to restrict processing
- Right to data portability
Learn more aboutyour data rights.
💡 Privacy Best Practices
Recommendations for maintaining your digital privacy:
- Review settings quarterly
- Use strong, unique passwords
- Enable two-factor authentication
- Be selective about shared information
- Regularly audit connected applications
🚨 Urgent Privacy Concerns?
Contact our privacy team immediately:
- Email: eliomondello@mondosol.com
- Subject: “Privacy Settings Assistance”
- Response Time: Within 24 hours
Your privacy is our priority. 🔐
Internal Resources
Leave a Reply
Discover your comprehensive data privacy rights at Mondosol. Learn how to access, correct, delete, and control your personal information with our transparent privacy framework.
Understanding your data privacy rights is crucial in today’s digital world. At Mondosol, we’re committed to transparency and empowering you with comprehensive control over your personal information.
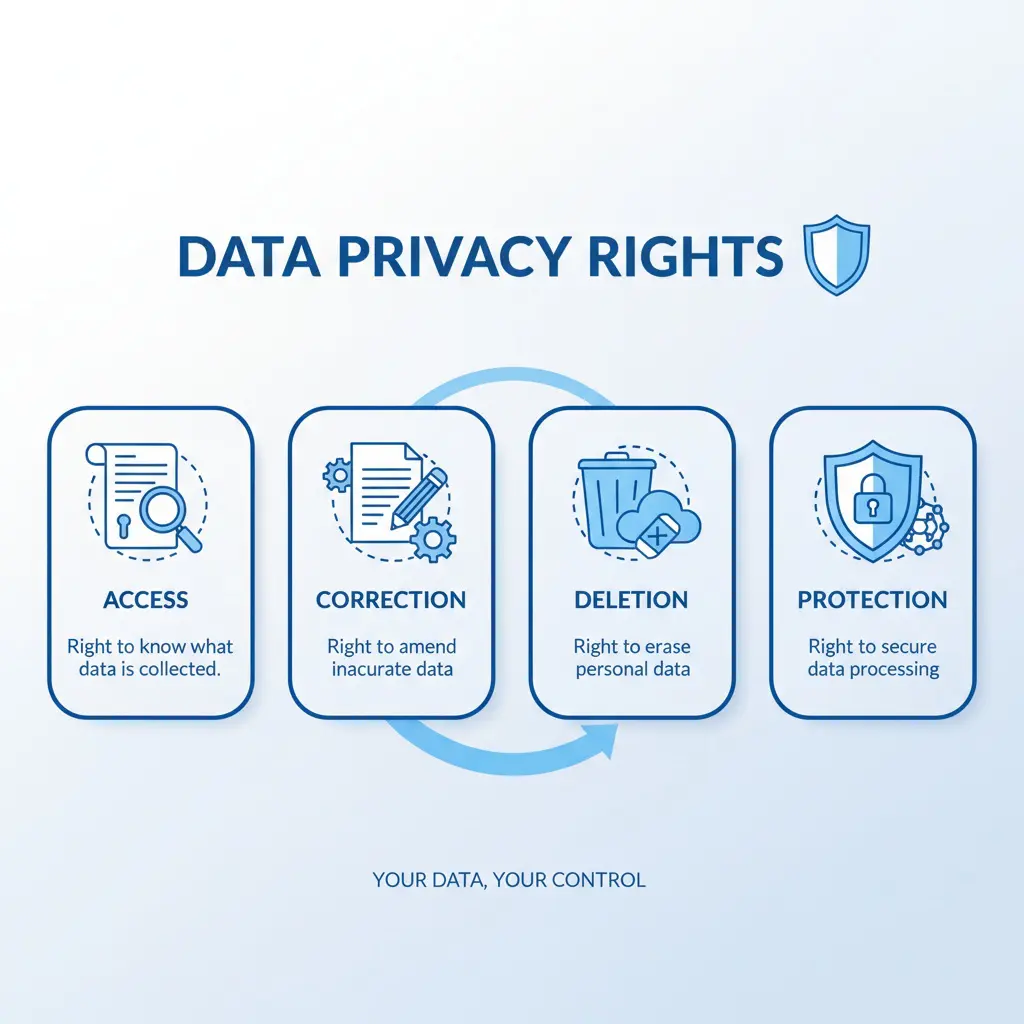
🛡️ Fundamental Data Privacy Rights
Your rights are not just legal requirements—they’re fundamental protections of your personal information. Here’s a comprehensive breakdown of the rights you have regarding your data.
Core Privacy Rights Framework
You have the following fundamental rights:
- Right to Access: Know what data we collect
- Right to Correction: Update inaccurate information
- Right to Deletion: Request removal of your data
- Right to Restrict Processing: Limit how we use your data
- Right to Data Portability: Receive your data in a usable format
- Right to Object: Oppose certain data processing activities
🔍 Right to Access Your Data
You have the right to know exactly what personal information we collect:
How to Request Your Data
- Email eliomondello@mondosol.com
- Subject: “Data Access Request”
- We’ll provide:
- Complete personal information we hold
- Sources of data collection
- Purpose of data processing
- Retention periods
Learn more aboutcomprehensive data access.

✏️ Right to Correction
Discovered inaccurate information? You can request corrections:
Correction Request Process
- Identify incorrect data
- Provide correct information
- Submit supporting documentation if necessary
- We’ll update your records within 30 days
According to the European Data Protection Board, timely and accurate data is a fundamental privacy right.
🗑️ Right to Deletion (Right to be Forgotten)
You can request complete removal of your personal data:
Deletion Scenarios
- When data is no longer necessary
- If you withdraw consent
- If data was processed unlawfully
- When you object to processing
Important Considerations:
- Some legal records may be retained
- Deletion is permanent and cannot be undone
- You may lose access to services dependent on that data
🛑 Right to Restrict Processing
You can limit how we use your personal data:
Processing Restriction Conditions
- During data accuracy verification
- When processing is unlawful
- When we no longer need the data
- While considering your objection to processing
📦 Right to Data Portability
Receive your data in a structured, machine-readable format:
Portability Features
- Export complete data profile
- Receive data in common formats (JSON, CSV)
- Transfer to another service provider
- Includes:
- Personal information
- Learning data
- Account history
🚫 Right to Object
You can object to certain data processing activities:
Objection Grounds
- Direct marketing
- Automated decision-making
- Processing for research purposes
- Legitimate interest processing
🌐 International Privacy Rights
Our commitment extends beyond regional regulations:
Global Privacy Standards
- GDPR (European Union)
- CCPA (California, USA)
- PIPEDA (Canada)
- APPI (Japan)
Learn more aboutinternational privacy standards.
Internal Resources
📞 Exercise Your Privacy Rights
Questions or want to exercise your rights?
- Email: eliomondello@mondosol.com
- Subject: “Privacy Rights Inquiry”
- Response Time: Within 24-48 hours
Your data, your control. 🔒
Leave a Reply
Discover what privacy regulations Mondosol follows including GDPR, CCPA, UK GDPR, PIPEDA, and international standards. Learn how we protect your data through comprehensive compliance with global privacy laws.
What Privacy Regulations Does Mondosol Follow? ⚖️
Navigating the complex world of privacy regulations can be overwhelming. At Mondosol, we simplify this by adhering to the world’s most stringent privacy standards, ensuring your data receives maximum protection regardless of where you live.
🌍 Global Privacy Compliance Framework
Rather than following minimum requirements, we adopt the highest privacy standards globally. This approach means that all users benefit from comprehensive protection, not just those in specific regions.

Our Compliance Philosophy
We believe privacy is a fundamental right, not a regional privilege. Therefore, we implement:
- Universal high standards for all users
- Proactive compliance with emerging regulations
- Transparent practices across all jurisdictions
- Regular audits to ensure ongoing compliance
🇪🇺 GDPR (General Data Protection Regulation)
The GDPR represents the gold standard in data protection. Implemented in May 2018, this European Union regulation sets comprehensive requirements for personal data handling.
GDPR Core Principles We Follow
Mondosol adheres to all seven GDPR principles:
Lawfulness, Fairness, and Transparency:
- We process data only with valid legal basis
- We inform you clearly about data collection
- We explain how we use your information
- We maintain transparent privacy policies
Purpose Limitation:
- We collect data for specific, explicit purposes
- We don’t repurpose data without your consent
- We document the reason for each data collection
- We limit processing to stated purposes
Data Minimization:
- We collect only necessary information
- We avoid excessive data gathering
- We regularly review what data we truly need
- We delete unnecessary information promptly
Accuracy:
- We maintain accurate and up-to-date records
- We provide tools for you to correct information
- We verify data accuracy regularly
- We update records when you notify us of changes
Storage Limitation:
- We retain data only as long as necessary
- We establish clear retention periods
- We delete data when no longer needed
- We document our retention policies
Integrity and Confidentiality:
- We implement robust security measures
- We encrypt sensitive information
- We protect against unauthorized access
- We train staff on data protection
Accountability:
- We document all processing activities
- We conduct regular compliance audits
- We maintain records of consent
- We report breaches within 72 hours
Learn more about GDPR from the European Commission.

Your GDPR Rights at Mondosol
Under GDPR, you have comprehensive rights:
- Right to Access: Request all data we hold about you
- Right to Rectification: Correct inaccurate information
- Right to Erasure: Request deletion of your data
- Right to Restrict Processing: Limit how we use your data
- Right to Data Portability: Receive your data in portable format
- Right to Object: Oppose certain processing activities
- Rights Related to Automated Decision-Making: Opt out of automated profiling
To exercise these rights, contact eliomondello@mondosol.com.
🇺🇸 CCPA (California Consumer Privacy Act)
The CCPA protects California residents with comprehensive privacy rights. Effective January 2020, this regulation grants significant control over personal information.
CCPA Rights We Honor
California users enjoy these specific rights to:
Know:
- What personal information we collect
- The sources of that information
- The purposes for collection
- Third parties we share with
Delete:
- Request deletion of personal information
- With exceptions for legal obligations
- Confirmed within 45 days
Opt-Out:
- Opt out of data sales (we don’t sell data)
- Control third-party sharing
- Manage marketing preferences
Non-Discrimination:
- Equal service regardless of privacy choices
- No penalties for exercising rights
- Same quality of service for all
Learn more about CCPA from the California Attorney General.
CPRA Enhancement
The California Privacy Rights Act (CPRA), effective January 2023, enhances CCPA with:
- Sensitive personal information protections
- Data minimization requirements
- Purpose limitation enforcement
- Enhanced enforcement mechanisms
We comply fully with both CCPA and CPRA requirements.
🇬🇧 UK GDPR and Data Protection Act 2018
Following Brexit, the UK implemented its own version of GDPR. We maintain compliance with UK-specific requirements:
UK-Specific Compliance
Our UK compliance includes:
- ICO registration and cooperation
- UK data transfer mechanisms
- British standards adherence
- Local representation for UK users
Learn more from the UK Information Commissioner’s Office.
🇨🇦 PIPEDA (Personal Information Protection and Electronic Documents Act)
Canada’s federal privacy law governs private sector data handling. We comply with PIPEDA through:
PIPEDA Compliance Measures
Our Canadian compliance includes:
- Consent requirements for data collection
- Purpose specification before collection
- Limited collection to necessary data
- Accuracy maintenance of records
- Safeguards for personal information
- Openness about privacy practices
- Individual access to personal data
- Challenging compliance mechanisms
Learn more about PIPEDA from the Office of the Privacy Commissioner of Canada.
🌏 APPI (Act on the Protection of Personal Information – Japan)
Japan’s privacy law underwent significant amendments in 2020. We comply with APPI requirements:
APPI Compliance Framework
Our Japanese compliance includes:
- Proper purpose specification
- Lawful acquisition of data
- Accurate maintenance of records
- Security management measures
- Transparent handling of data
- Cross-border transfer safeguards
🇦🇺 Australian Privacy Act
Australia’s Privacy Act governs how organizations handle personal information. We follow the Australian Privacy Principles (APPs):
APP Compliance
Our Australian compliance includes:
- Open and transparent management
- Anonymity and pseudonymity options
- Collection limitations to necessary data
- Use and disclosure restrictions
- Security safeguards implementation
- Access and correction mechanisms
Learn more from the Office of the Australian Information Commissioner.
🌐 Other Regional Privacy Laws
Beyond major regulations, we monitor and comply with emerging privacy laws:
Additional Compliance
We also follow:
- Brazil’s LGPD (Lei Geral de Proteção de Dados)
- South Africa’s POPIA (Protection of Personal Information Act)
- Singapore’s PDPA (Personal Data Protection Act)
- India’s proposed Data Protection Bill
- Various state-level US privacy laws

🏫 Educational Privacy Standards
As an educational platform, we also align with education-specific privacy frameworks:
FERPA Principles
Although FERPA technically applies to US educational institutions receiving federal funding, we adopt its best practices:
- Student consent for educational record disclosure
- Limited access to educational records
- Right to review and correct records
- Annual notification of rights
Learn about FERPA from the US Department of Education.
COPPA Compliance
The Children’s Online Privacy Protection Act protects children under 13. We comply by:
- Not knowingly collecting data from children under 13
- Requiring parental consent for underage users
- Providing parental access to children’s data
- Allowing parents to delete children’s information
Learn about COPPA from the Federal Trade Commission.
🔐 Industry-Specific Security Standards
Beyond privacy regulations, we follow security standards:
ISO 27001
We align with International Organization for Standardization security management:
- Information security management systems
- Risk assessment methodologies
- Security controls implementation
- Continuous improvement processes
SOC 2 Principles
We follow Service Organization Control principles:
- Security: Protection against unauthorized access
- Availability: System availability for operation
- Processing Integrity: Complete and accurate processing
- Confidentiality: Protected confidential information
- Privacy: Personal information collection and use
Learn about SOC 2 from the AICPA.
PCI DSS
For payment processing, we maintain Payment Card Industry Data Security Standard compliance:
- Secure network maintenance
- Cardholder data protection
- Vulnerability management programs
- Access control measures
- Network monitoring and testing
- Information security policies

📋 Compliance Documentation
We maintain comprehensive documentation demonstrating our compliance:
Available Documentation
Upon request, we provide:
- Privacy Impact Assessments (PIAs)
- Data Processing Agreements (DPAs)
- Records of Processing Activities (ROPA)
- Data Transfer Impact Assessments (DTIAs)
- Breach notification procedures
- Compliance audit reports
To request documentation, email eliomondello@mondosol.com with subject “Compliance Documentation Request.”
🔄 Continuous Compliance Monitoring
Privacy regulations constantly evolve. Therefore, we maintain ongoing compliance through:
Our Compliance Process
We ensure continuous compliance by:
- Monitoring regulatory changes globally
- Updating policies and procedures promptly
- Training staff on new requirements
- Conducting regular compliance audits
- Engaging external privacy consultants
- Participating in industry privacy forums
Compliance Team
Our dedicated privacy team:
- Reviews new regulations quarterly
- Assesses impact on our operations
- Implements necessary changes
- Documents compliance measures
- Reports to leadership regularly
🔗 Privacy Regulation Resources
Learn more about privacy regulations and your rights:
Internal Resources:
External Regulatory Resources:
- GDPR Official Portal – European data protection
- California Privacy Rights – CCPA information
- UK ICO – UK data protection authority
- IAPP Resources – International privacy professional association
📞 Privacy Compliance Questions?
If you have questions about our regulatory compliance:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Privacy Regulation Inquiry”
- Response Time: Within 24-48 hours
For specific compliance documentation:
- Subject: “Compliance Documentation Request”
- Include: Specific regulation or document needed
- Delivery: Within 30 days
Your privacy is protected by the world’s strongest regulations, and we’re committed to exceeding every standard. ⚖️🔒
Last Updated: October 8, 2025
Leave a Reply
Learn how to request your personal data from Mondosol. Step-by-step guide to submitting data access requests, understanding your data package, and exercising your privacy rights under GDPR, CCPA, and other regulations.
You have the absolute right to access all personal data we hold about you. At Mondosol, we’ve made the data request process simple, transparent, and efficient. In this comprehensive guide, we’ll walk you through every step of requesting, receiving, and understanding your personal information.
🔍 Understanding Data Access Rights
Your right to access personal data is fundamental under privacy regulations worldwide. This means you can request a complete copy of all information we’ve collected about you.

What Data You Can Request
When you request your data, you’ll receive comprehensive information including:
Personal Account Information:
- Full name and contact details
- Email address and phone number
- Account creation date and history
- Profile information and preferences
- Login credentials (encrypted, not plain text)
Learning and Course Data:
- Course enrollments and completion status
- Quiz results and assessment scores
- Certificates earned and achievements
- Learning progress across all courses
- Time spent on lessons and modules
Communication Records:
- Support tickets and correspondence
- Newsletter subscriptions and preferences
- Email communications we’ve sent
- Feedback and reviews you’ve submitted
Technical and Usage Data:
- Login history with dates and locations
- Device information used to access Mondosol
- IP addresses and browser details
- Activity logs showing platform interactions
Payment and Billing Information:
- Purchase history and transaction records
- Billing addresses and payment methods (last 4 digits only)
- Invoices and receipts for all purchases
- Refund records if applicable
According to privacy experts at the International Association of Privacy Professionals, comprehensive data access is essential for transparency and trust.
📧 How to Submit a Data Request
Requesting your data is straightforward. Follow these simple steps:
Step-by-Step Request Process
Step 1: Compose Your Email
Send your request to: eliomondello@mondosol.com
Subject Line: “Data Access Request”
Email Template:
Subject: Data Access Request
Dear Mondosol Privacy Team,
I am writing to request a complete copy of all personal data you hold about me under [GDPR/CCPA/applicable regulation].
Account Email: [your registered email]
Full Name: [your full name]
Additional Verification: [account creation date or last purchase, if known]
Please provide my data in a commonly used, machine-readable format.
Thank you,
[Your Name]
Step 2: Identity Verification
To protect your privacy, we verify your identity before releasing data:
- We’ll confirm your email address matches our records
- We may ask security questions about your account
- We might request additional verification for sensitive requests
- This process typically takes 1-2 business days
Why verification matters: According to the Federal Trade Commission, proper identity verification prevents unauthorized data access.
Step 3: Processing Time
We process data requests within regulatory timeframes:
- Standard processing: 30 days from verification
- Complex requests: Up to 60 days (we’ll notify you if extension needed)
- Simple requests: Often completed within 7-14 days
- Urgent requests: Contact us to discuss expedited processing

Step 4: Receiving Your Data
Once processed, we’ll deliver your data securely:
Delivery Methods:
- Secure email with encrypted attachment
- Password-protected ZIP file
- Secure download link (expires after 7 days)
- Physical mail upon request (additional processing time)
Data Formats:
- PDF for human-readable documents
- CSV for spreadsheet data
- JSON for machine-readable structured data
- Combined package with all formats
🔐 Security and Privacy During Requests
We take extraordinary measures to protect your data during the request process:
Security Measures
Throughout the process, we ensure:
- Encrypted transmission of all data files
- Secure storage of request documentation
- Access logging for accountability
- Automatic deletion of temporary files after delivery
- Verification protocols to prevent unauthorized access
Learn more about our security practices.
Privacy Protections
We protect your privacy by:
- Never sharing your request with third parties
- Limiting access to authorized privacy team members only
- Documenting all request handling procedures
- Maintaining confidentiality throughout the process
📊 Understanding Your Data Package
When you receive your data, here’s how to interpret it:
Data Package Contents
Your package typically includes:
1. Summary Document (PDF):
- Overview of all data categories
- Explanation of each data type
- Retention periods for different data
- Sources of data collection
2. Detailed Data Files:
- Account_Information.csv: Personal and profile data
- Learning_Records.csv: Course progress and results
- Communication_History.pdf: Email and support records
- Activity_Logs.csv: Login and usage history
- Payment_Records.pdf: Transaction and billing information
3. Metadata and Context:
- Data dictionary explaining field names
- Collection dates for each data point
- Legal basis for processing
- Retention schedules and deletion dates
Reading Your Data Files
Tips for understanding your data:
- Start with the summary document for an overview
- Use spreadsheet software (Excel, Google Sheets) for CSV files
- Check the data dictionary for unfamiliar terms
- Compare dates to understand data collection timeline
- Note retention periods to know when data will be deleted
If you need help interpreting your data, contact eliomondello@mondosol.com.
🔄 What Happens After Your Request
Beyond receiving your data, you have additional options:
Post-Request Actions
After reviewing your data, you can request :
Corrections:
- Identify any inaccurate information
- Submit correction requests with supporting documentation
- We’ll update records within 30 days
- Receive confirmation once corrections are made
Deletion:
- Decide if you want data deleted
- Submit a separate deletion request
- Understand that some data may be retained for legal compliance
- Receive confirmation of deletion within 30 days
Restrictions:
- Limit how we process certain data
- Temporarily suspend processing during disputes
- Maintain data without active use
- Resume processing only with your consent
To export to Another Service:
- Use machine-readable formats for portability
- Transfer data to competitors or other platforms
- Exercise your right to data portability
- Maintain a personal backup of your information
🌍 International Data Requests
Regardless of your location, we honor data access requests:
Region-Specific Considerations
European Union (GDPR):
- 30-day response time (extendable to 60 days)
- Free of charge for reasonable requests
- Machine-readable format provided
- Right to complain to supervisory authority
California (CCPA/CPRA):
- 45-day response time (extendable to 90 days)
- Twice yearly requests allowed
- No discrimination for exercising rights
- Specific categories of data disclosed
United Kingdom (UK GDPR):
- One month response time
- Free access to personal data
- ICO complaint option available
- Same rights as EU GDPR
Canada (PIPEDA):
- 30-day response time
- Reasonable cost may apply for extensive requests
- Privacy Commissioner complaint option
- Access to all personal information
Learn about regional privacy laws from OneTrust DataGuidance.

❓ Common Data Request Questions
Here are answers to frequently asked questions:
FAQ About Data Requests
Q: Is there a fee for requesting my data?
A: No, data requests are completely free for reasonable requests. However, if you make excessive or repetitive requests, we may charge a reasonable administrative fee or refuse the request.
Q: How often can I request my data?
A: You can request your data anytime. However, if you’ve recently received a complete data package, we may ask if you want an updated version rather than a full reprocessing.
Q: Can someone else request my data on my behalf?
A: Yes, with proper authorization. You must provide:
- Written consent authorizing the representative
- Proof of identity for both you and the representative
- Specific scope of what they can access
Q: What if I find errors in my data?
A: Contact us immediately with:
- Specific errors identified
- Correct information with supporting documentation
- We’ll investigate and correct within 30 days
Q: Can I request data for a deleted account?
A: It depends on timing. If your account was recently deleted:
- Within 30 days: We likely still have your data
- After 30 days: Data may be permanently deleted
- Legal retention: Some data kept for 7 years for compliance
Q: Will requesting my data affect my account?
A: No, absolutely not. Requesting your data:
- Doesn’t impact your account status
- Doesn’t affect your access to services
- Doesn’t change your subscription or enrollment
- Is completely confidential
🚨 Urgent Data Access Needs
If you need your data urgently due to legal proceedings or other time-sensitive matters:
Expedited Request Process
Contact us immediately:
- Email: eliomondello@mondosol.com
- Subject: “URGENT: Expedited Data Request”
- Include: Reason for urgency and deadline
We’ll prioritize:
- Legal proceedings: Court orders or subpoenas
- Data breaches: If you suspect unauthorized access
- Account disputes: Billing or service disagreements
- Regulatory investigations: Official inquiries
Expedited processing typically takes 3-7 business days instead of 30 days.
🔗 Related Data Rights Resources
Learn more about your data rights and privacy:
Internal Resources:
External Privacy Resources:
- GDPR Right to Access – European data access rights
- CCPA Data Access – California consumer rights
- Your Data Rights Guide – Comprehensive privacy information
- Data Portability Project – Understanding data portability
📞 Need Help With Your Data Request?
If you have questions about requesting your data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Data Request Assistance”
- Response Time: Within 24-48 hours
For technical issues:
- Subject: “Data Request Technical Support”
- Include: Error messages or specific problems
- Priority response: Within 12-24 hours
For legal or compliance questions:
- Subject: “Data Request Legal Inquiry”
- Include: Specific regulation or legal requirement
- Expert response: Within 48-72 hours
Your data belongs to you. We’re here to help you access it quickly, securely, and completely. 📋🔒
Last Updated: October 8, 2025
Leave a Reply
Account Management (1)
Comprehensive guide to managing your Mondosol privacy settings. Control profile visibility, data sharing, communication preferences, and protect your personal information with granular privacy controls.
Your privacy is in your hands at Mondosol. This comprehensive guide will walk you through every step of managing and customizing your privacy settings to ensure you have complete control over your personal information.
🔒 Privacy Settings Overview
Privacy management is more than just a few toggles—it’s about giving you total control over your digital experience. At Mondosol, we provide granular, easy-to-use privacy controls across multiple dimensions of your account.

Key Privacy Control Areas
You can manage privacy settings in these critical areas:
- Profile Visibility
- Data Sharing Preferences
- Communication Permissions
- Third-Party Integrations
- Content Visibility
- Activity Tracking
🛠️ Accessing Your Privacy Dashboard
To manage your privacy settings, follow these step-by-step instructions:
- Log into your Mondosol account
- Navigate to Settings → Privacy Controls
- Review each section carefully
- Make selections that feel comfortable for you
Pro Tip: Learn more about account security before adjusting settings.
Profile Visibility Options
Control who sees your personal information:
Visibility Levels:
- Public: Anyone can view your profile
- Mondosol Members Only: Visible to registered users
- Private: Completely hidden from other users
- Custom: Create granular visibility rules

Alt text: Multiple privacy levels for controlling profile information visibility
📊 Data Sharing Preferences
Decide exactly how your data is used:
Analytics and Improvement Programs
Choose your level of data contribution:
- Full Participation: Help improve Mondosol’s services
- Limited Sharing: Anonymized data only
- No Participation: Opt-out of all data collection
According to Electronic Frontier Foundation, informed consent is crucial in data sharing.
Third-Party Integration Controls
Manage connections with external services:
Review Connected Apps:
- View all connected applications
- Revoke access for unused or suspicious integrations
- Control what information each app can access
🔔 Communication Permissions
Take control of how and when we communicate:
Email Notification Settings
Customize your communication preferences:
Notification Types:
- Course Updates
- Marketing Communications
- Security Alerts
- Community Notifications
- Promotional Offers
Each category can be individually enabled or disabled.
🌐 International Privacy Compliance
We adhere to global privacy standards:
GDPR and CCPA Compliance
Your rights are protected by:
- Right to access your data
- Right to deletion
- Right to restrict processing
- Right to data portability
Learn more aboutyour data rights.
💡 Privacy Best Practices
Recommendations for maintaining your digital privacy:
- Review settings quarterly
- Use strong, unique passwords
- Enable two-factor authentication
- Be selective about shared information
- Regularly audit connected applications
🚨 Urgent Privacy Concerns?
Contact our privacy team immediately:
- Email: eliomondello@mondosol.com
- Subject: “Privacy Settings Assistance”
- Response Time: Within 24 hours
Your privacy is our priority. 🔐
Internal Resources
Leave a Reply
Account Security (1)
Discover immediate steps to take if you suspect unauthorized access to your Mondosol account. Learn how to secure your account, detect suspicious activity, and prevent future security breaches
DiscovDiscovering unauthorized access to your Mondosol account can be stressful. If you suspect someone has accessed your account without permission, follow these critical steps to protect your unauthorized account access and secure your personal information immediately.
🔴 Immediate Steps for Unauthorized Account Access
1. Change Your Password for Account Security
- Quickly log into your Mondosol account security settings
- Create a strong, unique password to prevent unauthorized access
- Use a combination of letters, numbers, and symbols

2. Detect and Remove Unauthorized Sessions
- Go to Settings → Security
- Review login history
- Click Sign Out Everywhere to block unauthorized access
- Check for suspicious login locations or devices
🕵️ Identifying Unauthorized Account Access
Signs of Potential Security Breach
- Unfamiliar login locations
- Unexpected account changes
- Unauthorized purchases
- Suspicious email notifications
🛡️ Comprehensive Account Protection Strategies
Enable Two-Factor Authentication
- Set up 2FA
- Choose between authenticator app or SMS
- Add an extra layer of unauthorized access prevention

Monitor Account Activity
- Regularly check account activity logs
- Set up security alerts
- Review connected applications
📞 Get Immediate Security Support
Urgent Unauthorized Access Concerns:
- Email: security@mondosol.com
- Emergency Response: Within 24 hours
- Provide detailed information about suspected unauthorized access
Quick action protects your account and personal data from unauthorized access. 🔐
📞 Professional Security Support
Need Expert Assistance?
- Contact Cybersecurity Experts:
- External Security Verification:
🔗 Related Security Resources
Leave a Reply
Data Protection (8)
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Transparency is the foundation of trust. We believe you have the right to know exactly what information we collect, why we collect it, and how we use it. Here’s a complete breakdown of the personal data Mondosol collects.
👤 Account Information
When you create a Mondosol account, we collect:
Required Information
- Full Name: To personalize your experience and address you properly
- Email Address: For account verification, login, and important communications
- Username: Your unique identifier on the platform
- Password: Encrypted and never stored in plain text
Optional Information
- Profile Picture: To personalize your learning profile
- Bio/Description: To share information with the community
- Location/Country: To provide localized content and comply with regional regulations
- Language Preferences: To deliver content in your preferred language(s)
Why We Collect This: To create and manage your account, verify your identity, and provide personalized services.
📚 Learning & Course Data
To track your progress and improve your learning experience:
Course Activity
- Enrollment Dates: When you start each course
- Progress Tracking: Lessons completed, modules finished
- Time Spent: Duration on each lesson and course
- Completion Status: Courses finished and certificates earned
Assessment Data
- Quiz Results: Scores and answers (for feedback and improvement)
- Assignment Submissions: Your work and instructor feedback
- Test Performance: Assessment results and analytics
Learning Preferences
- Course Interests: Topics you’re interested in
- Learning Goals: Your stated objectives
- Skill Levels: Self-reported or assessed proficiency
- Preferred Learning Pace: Fast-track or standard progression
Why We Collect This: To track your progress, provide certificates, personalize recommendations, and improve course content.
💳 Payment & Billing Information
When you make a purchase:
Billing Details
- Billing Name: Name on payment method
- Billing Address: Required for payment processing
- Country/Region: For tax calculations and compliance
- VAT/Tax ID: If applicable for business purchases
Payment Information
- Payment Method Type: Credit card, PayPal, etc.
- Last 4 Digits: For payment method identification
- Transaction History: Purchase dates, amounts, and order details
Important: We never store complete credit card numbers. All payment processing is handled by certified third-party processors (Stripe, PayPal) that are PCI DSS compliant.
Why We Collect This: To process payments, issue invoices, handle refunds, and comply with financial regulations.
💻 Technical & Usage Data
To improve platform performance and user experience:
Device Information
- IP Address: For security, fraud prevention, and geographic content delivery
- Browser Type & Version: To ensure compatibility
- Operating System: To optimize platform performance
- Device Type: Desktop, mobile, or tablet for responsive design
Usage Analytics
- Pages Visited: Which pages you view and how often
- Click Patterns: What buttons and links you interact with
- Session Duration: How long you spend on the platform
- Referral Source: How you found Mondosol (search, social media, direct)
Cookies & Tracking
- Essential Cookies: Required for platform functionality
- Analytics Cookies: To understand user behavior (you can opt-out)
- Marketing Cookies: For personalized advertising (you can opt-out)
Why We Collect This: To improve platform performance, fix bugs, understand user behavior, and enhance user experience.
📧 Communication Data
When you interact with us:
Email Communications
- Support Tickets: Your questions and our responses
- Newsletter Subscriptions: Topics you’re interested in
- Marketing Preferences: What communications you want to receive
- Unsubscribe Requests: Your opt-out preferences
Community Interactions
- Comments & Reviews: Your feedback on courses
- Forum Posts: Community discussions and contributions
- Messages: Direct communications with instructors or support
Why We Collect This: To provide customer support, send requested information, and facilitate community interaction.
🤝 Social Media & Third-Party Data
If you connect social accounts or use third-party services:
- Social Profile Information: Name, profile picture, email (if you sign up via Facebook, Google, LinkedIn)
- Third-Party Integrations: Data from connected apps (with your permission)
- Affiliate Tracking: If you arrive through an affiliate link
Why We Collect This: To simplify account creation, enable social sharing, and track affiliate referrals.
🚫 What We DON’T Collect
We respect your privacy and never collect:
- ❌ Sensitive personal data (race, religion, political views, health information)
- ❌ Data from children under 13 without parental consent
- ❌ Information from your device without permission
- ❌ Data unrelated to our services
- ❌ Information we don’t need for legitimate purposes
📊 How Long We Keep Your Data
We follow data minimization principles:
- Active Accounts: Data retained while your account is active
- Inactive Accounts: Deleted after 3 years of inactivity (with prior notice)
- Legal Requirements: Some data retained longer for legal/tax compliance (typically 7 years)
- Marketing Data: Removed immediately upon unsubscribe
- Right to Erasure: You can request deletion anytime
🔒 Your Data Rights
You have complete control over your data:
- Access: Request a copy of all data we hold
- Correction: Update inaccurate information
- Deletion: Request complete data removal
- Portability: Receive your data in machine-readable format
- Objection: Opt-out of certain data processing
Learn more about your data rights →
🔗 Related Resources
Privacy & Security:
External Resources:
- GDPR Data Collection Guidelines – European standards
- CCPA Consumer Rights – California privacy law
- ICO Data Protection Guide – UK regulations
📞 Questions About Your Data?
We’re committed to transparency. If you have questions about what data we collect:
- Email: eliomondello@mondosol.com
- Subject: “Data Collection Inquiry”
- Response Time: Within 24 hours
We collect only what we need, protect what we collect, and respect your choices. 🔒
Last Updated: October 8, 2025
Leave a Reply
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Your personal information deserves the highest level of protection. At Mondosol, we implement comprehensive security measures to ensure your data remains safe, private, and secure at all times. In this guide, we’ll walk you through every layer of protection we’ve built to safeguard your information.
🛡️ Our Multi-Layer Security Approach
Rather than relying on just one security measure, we use multiple layers of protection to safeguard your personal information. As a result, your data benefits from redundant security systems that work together seamlessly.
SSL/TLS Encryption
First and foremost, we encrypt all data transmitted between your device and our servers using industry-standard SSL/TLS protocols. Consequently, your information becomes scrambled during transmission, making it unreadable to unauthorized parties.
In practice, this means:
- When you log in, your password travels encrypted through the internet
- Similarly, when you submit course work, the content remains protected
- Additionally, all payment information transfers through secure channels
- Therefore, hackers cannot intercept your data even if they access the network
To verify this protection, always look for the padlock icon in your browser’s address bar when using Mondosol. Furthermore, you can click the padlock to view our security certificate details.
Secure Server Infrastructure
Beyond encryption in transit, we also protect your data at rest. Specifically, we store your personal data on secure servers with restricted physical and digital access.
To accomplish this, we implement several protective measures:
- State-of-the-art firewalls protect against unauthorized intrusion attempts
- In addition, our 24/7 server monitoring detects and responds to potential threats in real-time
- Moreover, we maintain physical security at our data centers with biometric access controls
- As an extra precaution, we conduct regular security perimeter assessments
As a result of these measures, your data remains protected even when you’re not actively using the platform.
Data Encryption at Rest
Not only do we encrypt data during transmission, but also when we store it on our servers. In other words, your sensitive information stays encrypted whether it’s moving or sitting in our database.
To enhance this protection further, we implement additional safeguards:
- First, we manage encryption keys separately from the data itself
- Second, we rotate encryption keys regularly to minimize risk
- Third, we require multi-factor authentication for all system access
- Finally, we maintain encrypted backups in geographically separate locations
Therefore, even in the unlikely event of a server breach, your data remains unreadable without the encryption keys.
🔍 Regular Security Audits & Testing
Rather than waiting for problems to occur, we proactively identify and address vulnerabilities through comprehensive testing programs.
Quarterly Security Assessments
Every three months, independent security experts thoroughly review our systems. During these assessments, they:
- First, examine our infrastructure for potential weaknesses
- Then, test our security protocols against current threat models
- Subsequently, provide detailed recommendations for improvements
- Finally, verify that we’ve implemented previous recommendations
As a result, we stay ahead of emerging security threats and maintain industry-leading protection standards.
Penetration Testing
In addition to audits, we conduct regular penetration testing. Essentially, this means we hire ethical hackers to attempt breaking into our systems. Through this process, we:
- Initially, simulate real-world attack scenarios
- Next, identify vulnerabilities before malicious actors can exploit them
- Then, patch any discovered weaknesses immediately
- Ultimately, strengthen our defenses based on test results
Consequently, our security improves continuously through controlled testing.
Vulnerability Scanning
Beyond manual testing, automated tools continuously monitor for security gaps. Specifically, these systems:
- Constantly scan for known vulnerabilities in our software
- Immediately alert our security team when they detect potential issues
- Subsequently, trigger automatic patching for critical vulnerabilities
- Finally, generate reports for our security review process
Therefore, we can respond to new threats within hours rather than days or weeks.
Code Reviews
Before deploying any updates, our team conducts security-focused code reviews. During this process, we:
- First, examine all new code for security vulnerabilities
- Then, verify compliance with security best practices
- Additionally, test for common attack vectors like SQL injection
- Finally, require approval from multiple security team members
As a result, we prevent security issues from reaching our production environment.
📊 Data Minimization Principle
Unlike many platforms that collect excessive information, we only collect what we truly need. In fact, this principle guides every data collection decision we make.
Purpose Limitation
Specifically, we collect data only for specific, legitimate purposes. For example:
- When you create an account, we collect your email for login and communication
- Similarly, when you enroll in a course, we track your progress for certification
- However, we never collect data “just in case” we might need it later
- Instead, every data point serves a clear, documented purpose
Therefore, we minimize the amount of personal information at risk.
Storage Limitation
Furthermore, we retain information only as long as necessary. In practice, this means:
- Active account data remains available while you use our services
- However, after three years of inactivity, we send deletion notices
- Subsequently, we remove inactive account data unless you respond
- Additionally, we delete temporary data like session tokens immediately after use
As a result, we don’t accumulate unnecessary personal information over time.
Regular Data Purging
In addition to automated deletion, we conduct regular data purging reviews. During these reviews, we:
- First, identify outdated or unnecessary information
- Then, verify that legal retention requirements don’t apply
- Next, securely delete the identified data using military-grade methods
- Finally, document the deletion for compliance purposes
Consequently, your data footprint remains minimal and manageable.
No Excessive Collection
Most importantly, we never ask for information we don’t need. For instance:
- We don’t request your social security number or national ID
- Similarly, we don’t collect sensitive data about race, religion, or health
- Instead, we limit collection to essential account and learning information
- Therefore, you share only what’s necessary for your educational experience
As a result, you maintain greater privacy and control over your personal information.
👥 Strict Access Controls
Not everyone can access your data. In fact, we implement rigorous access controls to ensure only authorized personnel can view your information.
Role-Based Access
First and foremost, team members access only the data necessary for their specific role. For example:
- Customer support can view account details but not payment information
- Meanwhile, instructors see only their students’ course progress
- Similarly, developers access anonymized test data, not production information
- In contrast, only senior security personnel can access full system logs
Therefore, we minimize the number of people who can view your complete profile.
Authentication Protocols
Beyond role restrictions, we implement multi-factor authentication for all system access. Specifically, this means:
- First, employees must enter their password
- Then, they must provide a second factor (authenticator app or hardware token)
- Additionally, they must access systems from approved devices only
- Furthermore, suspicious login attempts trigger immediate security reviews
As a result, unauthorized individuals cannot access our systems even if they steal a password.
Activity Logging
To ensure accountability, we log and monitor all data access. In practice, this means:
- Every time someone views your data, we record who, when, and why
- Subsequently, security systems analyze these logs for unusual patterns
- If suspicious activity occurs, automated alerts notify our security team immediately
- Finally, we retain these logs for audit and compliance purposes
Consequently, we can detect and investigate any unauthorized access attempts.
Background Checks
Before hiring, all employees undergo comprehensive security clearance checks. This process includes:
- First, criminal background verification
- Then, employment history validation
- Additionally, reference checks from previous employers
- Finally, security training and confidentiality agreement signing
Therefore, we ensure that only trustworthy individuals handle your data.
Confidentiality Agreements
In addition to background checks, legal obligations ensure we protect your privacy. Specifically:
- All employees sign comprehensive confidentiality agreements
- These agreements legally bind them to protect user data
- Furthermore, violations result in immediate termination and legal action
- Moreover, these obligations continue even after employment ends
As a result, your data remains protected by both technical and legal safeguards.
💾 Secure Backup Systems
To protect against data loss, we maintain robust backup systems. However, these backups receive the same security protection as your live data.
Encrypted Backups
First and foremost, we fully encrypt all backups using the same standards as production data. This means:
- Even if someone steals backup media, they cannot read the data
- Additionally, we use separate encryption keys for backups and production
- Furthermore, we rotate backup encryption keys on a regular schedule
- Therefore, your historical data remains as secure as your current information
Geographic Redundancy
Beyond encryption, we store backups in multiple secure locations. Specifically:
- Primary backups reside in our main data center
- Secondary backups exist in a geographically separate facility
- Additionally, we maintain offline backups for disaster recovery
- Moreover, all backup locations meet the same security standards
As a result, your data survives even catastrophic events like natural disasters.
Regular Testing
Unlike many organizations, we don’t just create backups—we test them. In fact, we test backup restoration procedures monthly to verify effectiveness. During these tests, we:
- First, select random backup files for restoration
- Then, restore them to a test environment
- Next, verify data integrity and completeness
- Finally, document any issues and implement improvements
Consequently, we know our backups will work when we need them.
Disaster Recovery Plan
In addition to backups, we maintain a comprehensive disaster recovery plan. This plan ensures:
- First, we can restore services within hours of any incident
- Second, your data remains accessible even during emergencies
- Third, we maintain business continuity during disasters
- Finally, we communicate clearly with users during any service interruptions
Therefore, you can trust that your learning progress and data remain safe.
🔐 Payment Security
Because financial information requires special protection, we implement additional security measures for all payment processing.
PCI DSS Compliance
First and foremost, we follow Payment Card Industry Data Security Standards (PCI DSS). In practice, this means:
- We undergo annual security assessments by certified auditors
- Additionally, we maintain network segmentation to isolate payment systems
- Furthermore, we implement strict access controls for payment data
- Moreover, we conduct quarterly network vulnerability scans
As a result, your payment information receives bank-level security protection.
Third-Party Processors
Rather than handling payments directly, we process all transactions through certified secure providers like Stripe and PayPal. This approach offers several advantages:
- First, these processors specialize in payment security
- Second, they maintain PCI DSS Level 1 certification (the highest standard)
- Additionally, they handle fraud detection and prevention
- Furthermore, they assume liability for payment security
Therefore, your financial information benefits from industry-leading protection.
No Card Storage
Most importantly, we never store complete credit card numbers. Instead:
- Payment processors store your card details securely
- We receive only the last four digits for display purposes
- Additionally, we never see or store CVV security codes
- Furthermore, we cannot access your full payment information
Consequently, even if someone breaches our systems, they cannot steal your credit card data.
Tokenization
In addition to not storing cards, we replace payment information with secure tokens. Essentially, this means:
- When you save a payment method, we receive a random token
- This token references your card without containing actual card data
- Subsequently, we use this token for future transactions
- However, the token is useless to anyone except our payment processor
Therefore, your payment information remains protected through multiple security layers.
📱 Additional Security Measures
Beyond the core protections, we implement several additional security measures to safeguard your data.
GDPR Compliance
First, we maintain full compliance with EU General Data Protection Regulation (GDPR). This means:
- We respect all your data rights (access, deletion, portability)
- Additionally, we obtain clear consent before collecting data
- Furthermore, we process data lawfully and transparently
- Moreover, we report any breaches within 72 hours
Therefore, you benefit from Europe’s strongest privacy protections regardless of your location.
Privacy by Design
Rather than adding security later, we build it into every feature from the ground up. In practice, this means:
- When designing new features, we consider privacy implications first
- Subsequently, we implement privacy-protective defaults
- Additionally, we minimize data collection in all new features
- Finally, we conduct privacy impact assessments before launch
As a result, security and privacy are fundamental to our platform, not afterthoughts.
Incident Response Plan
In case of security incidents, we maintain rapid response procedures. Our plan includes:
- Immediate containment protocols to limit damage
- Subsequently, forensic investigation to understand the scope
- Then, user notification within required timeframes
- Finally, remediation and prevention of future incidents
Therefore, we can respond quickly and effectively to any security event.
User Education
Because security is a partnership, we provide resources to help you protect your own account. These resources include:
- Security best practices guides and tutorials
- Regular updates about emerging threats
- Additionally, tips for creating strong passwords
- Furthermore, guidance on recognizing phishing attempts
Consequently, you can take an active role in protecting your account.
Regular Updates
Finally, we keep our systems and software current with security patches. Specifically:
- We monitor security bulletins from all our software vendors
- Then, we test patches in our development environment
- Subsequently, we deploy critical patches within 24-48 hours
- Additionally, we conduct regular system updates during maintenance windows
As a result, we protect against newly discovered vulnerabilities quickly.
🚨 What We Do in Case of a Breach
In the unlikely event of a security breach, we take immediate and comprehensive action to protect you.
Immediate Containment
First and foremost, we isolate the threat within minutes of detection. This involves:
- Immediately, our automated systems detect unusual activity
- Then, they trigger containment protocols automatically
- Subsequently, our security team assesses the situation
- Finally, we implement additional manual containment measures
Therefore, we minimize the potential impact of any security incident.
Investigation
Once contained, we conduct thorough forensic analysis to understand the scope. During this investigation, we:
- First, determine what data the attackers accessed
- Then, identify how they gained access
- Next, assess the extent of the compromise
- Finally, document all findings for regulatory reporting
Consequently, we understand exactly what happened and can respond appropriately.
User Notification
In accordance with GDPR, we notify affected users within 72 hours. Our notification includes:
- First, a clear explanation of what happened
- Then, details about what data was affected
- Additionally, steps we’re taking to address the issue
- Furthermore, recommendations for protecting yourself
- Finally, contact information for questions and support
Therefore, you receive timely and transparent communication about any incidents affecting your data.
Remediation
After notification, we patch vulnerabilities immediately. This process includes:
- First, fixing the specific vulnerability that was exploited
- Then, conducting a comprehensive security review
- Subsequently, implementing additional protective measures
- Finally, retesting to ensure the issue is fully resolved
As a result, we prevent similar incidents from occurring in the future.
Transparency
Throughout the process, we ensure full disclosure of what happened and our response. Specifically, we:
- Publish detailed incident reports on our website
- Additionally, update users regularly as we learn more
- Furthermore, share lessons learned with the security community
- Moreover, implement recommended improvements from external experts
Therefore, we maintain accountability and continuously improve our security posture.
🔗 Related Resources
To learn more about your security and privacy, explore these helpful resources:
Last Updated: October 8, 2025
Leave a Reply
Discover immediate steps to take if you suspect unauthorized access to your Mondosol account. Learn how to secure your account, detect suspicious activity, and prevent future security breaches
DiscovDiscovering unauthorized access to your Mondosol account can be stressful. If you suspect someone has accessed your account without permission, follow these critical steps to protect your unauthorized account access and secure your personal information immediately.
🔴 Immediate Steps for Unauthorized Account Access
1. Change Your Password for Account Security
- Quickly log into your Mondosol account security settings
- Create a strong, unique password to prevent unauthorized access
- Use a combination of letters, numbers, and symbols

2. Detect and Remove Unauthorized Sessions
- Go to Settings → Security
- Review login history
- Click Sign Out Everywhere to block unauthorized access
- Check for suspicious login locations or devices
🕵️ Identifying Unauthorized Account Access
Signs of Potential Security Breach
- Unfamiliar login locations
- Unexpected account changes
- Unauthorized purchases
- Suspicious email notifications
🛡️ Comprehensive Account Protection Strategies
Enable Two-Factor Authentication
- Set up 2FA
- Choose between authenticator app or SMS
- Add an extra layer of unauthorized access prevention

Monitor Account Activity
- Regularly check account activity logs
- Set up security alerts
- Review connected applications
📞 Get Immediate Security Support
Urgent Unauthorized Access Concerns:
- Email: security@mondosol.com
- Emergency Response: Within 24 hours
- Provide detailed information about suspected unauthorized access
Quick action protects your account and personal data from unauthorized access. 🔐
📞 Professional Security Support
Need Expert Assistance?
- Contact Cybersecurity Experts:
- External Security Verification:
🔗 Related Security Resources
Leave a Reply
Discover how Mondosol protects your learning data with encryption, access controls, and privacy-focused practices. Learn about your rights to access, correct, and delete your educational records while maintaining complete privacy.
Your learning journey is personal and private. At Mondosol, we understand that your course progress, quiz results, and educational achievements deserve the highest level of protection. In this comprehensive guide, we’ll explain exactly how we safeguard your learning data and ensure your educational privacy.
🔒 Understanding Your Learning Data
Before diving into protection measures, let’s clarify what learning data includes and why protecting it matters.
What Constitutes Learning Data?
Your learning data encompasses all information related to your educational activities on Mondosol:
Course Activity Information:
- Enrollment dates for each course you join
- Progress tracking showing completed lessons and modules
- Time spent on each lesson and course section
- Completion status indicating finished courses
- Certificates earned upon course completion
Assessment and Performance Data:
- Quiz results including scores and answers
- Assignment submissions and instructor feedback
- Test performance across all assessments
- Practice exercise results and attempts
- Skill assessments measuring your proficiency levels
Learning Preferences and Behavior:
- Course interests and topics you explore
- Learning pace preferences (fast-track or standard)
- Study patterns showing when you’re most active
- Content interactions like bookmarks and notes
- Video playback preferences and watch history
According to educational privacy experts at the Student Privacy Compass, protecting learning data is essential for maintaining trust and encouraging honest educational engagement.

🛡️ Multi-Layer Learning Data Protection
Rather than relying on single security measures, we implement multiple protection layers specifically designed for learning data security.
Encryption for Learning Data
First and foremost, we encrypt all your learning data both in transit and at rest:
Data in Transit:
- When you submit quiz answers, we encrypt them using SSL/TLS protocols
- Similarly, course progress updates travel through secure, encrypted channels
- Additionally, all API communications use industry-standard encryption
- Therefore, no one can intercept your learning data during transmission
Data at Rest:
- We encrypt all stored learning data using AES-256 encryption
- Furthermore, we maintain separate encryption keys for different data types
- Moreover, we rotate encryption keys regularly to enhance security
- As a result, your learning records remain unreadable without proper authorization
Research from the National Institute of Standards and Technology emphasizes that encryption is fundamental to protecting sensitive educational records.
Access Control for Educational Records
Not everyone at Mondosol can view your learning data. Instead, we implement strict role-based access controls:
Who Can Access Your Learning Data:
- You: Full access to all your learning records and progress
- Your instructors: Limited access to your performance in their specific courses only
- Support staff: Restricted access only when assisting with technical issues
- System administrators: Encrypted, logged access for maintenance purposes only
Who Cannot Access Your Learning Data:
- ❌ Other students or community members
- ❌ Marketing teams or sales personnel
- ❌ Third-party advertisers or partners
- ❌ Anyone outside Mondosol without your explicit consent
Additionally, we log every instance when someone accesses your learning data, creating a complete audit trail for accountability.

Secure Database Infrastructure
Beyond encryption and access controls, we protect your learning data through robust infrastructure:
Database Security Measures:
- Dedicated servers specifically for educational records
- Firewall protection preventing unauthorized network access
- Regular security audits by independent cybersecurity experts
- Automated backups stored in geographically separate locations
- Disaster recovery systems ensuring data availability
According to database security standards from OWASP, layered security approaches provide the strongest protection for sensitive information.
📊 Learning Data Privacy Practices
Beyond technical security, we implement privacy-focused practices that respect your educational journey.
Data Minimization for Learning Records
We only collect learning data that directly supports your educational experience:
What We Collect and Why:
- Course progress: To show you where you left off and track completion
- Quiz scores: To provide feedback and generate certificates
- Time spent: To optimize course pacing and content length
- Learning preferences: To personalize recommendations
What We Don’t Collect:
- ❌ Unnecessary personal information unrelated to learning
- ❌ Behavioral data for advertising purposes
- ❌ Information about other websites you visit
- ❌ Data from your device beyond what’s needed for platform functionality
Therefore, we minimize your data footprint while maximizing your learning experience.
Anonymized Analytics for Course Improvement
When we analyze learning data to improve courses, we use anonymization techniques:
How We Anonymize Data:
- Remove all personally identifiable information
- Aggregate data across multiple students
- Use statistical methods that prevent re-identification
- Ensure individual students cannot be identified from reports
For example, we might analyze:
- “75% of students complete Module 3 in under 2 hours” ✅
- But never: “John Smith spent 3 hours on Module 3” ❌
Research from the Future of Privacy Forum explains how anonymization protects student privacy while enabling educational improvements.
Instructor Access Limitations
Even your course instructors have limited access to your learning data:
What Instructors Can See:
- ✅ Your progress in their specific course only
- ✅ Your quiz and assignment submissions for grading
- ✅ Your participation in course discussions
- ✅ Your completion status and certificates earned
What Instructors Cannot See:
- ❌ Your activity in other instructors’ courses
- ❌ Your personal contact information (unless you share it)
- ❌ Your payment or billing information
- ❌ Your overall account activity across Mondosol
Furthermore, instructors must agree to strict confidentiality terms before accessing any student data.

🎓 FERPA and Educational Privacy Compliance
As an educational platform, we align our practices with educational privacy regulations, particularly FERPA principles.
FERPA-Aligned Practices
Although FERPA technically applies to U.S. educational institutions receiving federal funding, we adopt its best practices:
FERPA Principles We Follow:
- Student consent: We obtain your permission before sharing learning data
- Limited disclosure: We don’t share educational records without authorization
- Access rights: You can review and request corrections to your learning data
- Security safeguards: We protect educational records from unauthorized access
Learn more about educational privacy rights from the U.S. Department of Education.
International Educational Privacy Standards
Beyond U.S. standards, we comply with international educational privacy requirements:
GDPR Compliance for Learning Data:
- Lawful basis: We process learning data based on contract performance
- Purpose limitation: Data used only for educational purposes
- Data minimization: Collect only necessary learning information
- Storage limitation: Retain data only as long as needed
According to the European Data Protection Board, educational data requires special protection under GDPR.
🔐 Your Control Over Learning Data
You maintain complete control over your learning data throughout your educational journey.
Accessing Your Learning Data
At any time, you can request a complete copy of your learning data:
How to Request Your Learning Data:
- Email eliomondello@mondosol.com
- Subject line: “Learning Data Access Request”
- Include your account email and full name
- Receive your data within 30 days in a readable format
Your data export includes:
- Complete course enrollment history
- All quiz and assessment results
- Certificates and completion records
- Learning preferences and settings
- Progress tracking across all courses
Correcting Learning Data Errors
If you discover inaccuracies in your learning records, you can request corrections:
Common Corrections:
- Quiz scores recorded incorrectly due to technical issues
- Completion status not updating properly
- Certificate information containing errors
- Progress tracking showing incorrect data
To request corrections:
- Contact your course instructor for course-specific issues
- Email support at eliomondello@mondosol.com for technical problems
- Provide specific details about the error
- Receive confirmation once we’ve made corrections
Deleting Your Learning Data
You have the right to request deletion of your learning data:
What Happens When You Delete:
- We remove all your course progress and quiz results
- We delete your certificates and completion records
- We erase your learning preferences and history
- However, we may retain anonymized data for analytics
Important considerations:
- Deletion is permanent and cannot be undone
- You’ll lose all progress and certificates
- You may need to restart courses from the beginning
- Some data may be retained for legal compliance (typically 7 years)
To request deletion:
- Email eliomondello@mondosol.com
- Subject: “Learning Data Deletion Request”
- We’ll process your request within 30 days

Alt text: Student control over learning data including access, correction, and deletion rights
🚫 What We Never Do With Learning Data
To maintain your trust, we make these absolute commitments about your learning data:
We Never Sell Your Learning Data
Unlike some educational platforms, we never sell your learning data to third parties:
- ❌ No data brokers: We don’t sell to data aggregation companies
- ❌ No advertisers: We don’t share learning data for targeted advertising
- ❌ No marketing lists: We don’t sell your information to marketers
- ❌ No third-party analytics: We don’t share identifiable data with external analytics companies
According to a report by the Electronic Frontier Foundation, selling student data undermines educational trust and privacy.
We Never Use Learning Data for Discrimination
Your learning data will never be used against you:
- ❌ Employment decisions: We don’t share data with potential employers without your consent
- ❌ Credit decisions: Learning performance doesn’t affect credit ratings
- ❌ Insurance: Your course activity won’t impact insurance premiums
- ❌ Admissions: We don’t share data with educational institutions without permission
We Never Share Learning Data Publicly
Your educational journey remains private:
- ❌ No public leaderboards: We don’t display your performance publicly without consent
- ❌ No social sharing: We don’t automatically post your progress to social media
- ❌ No public profiles: Your learning data isn’t visible in search engines
- ❌ No community exposure: Other students can’t see your quiz scores or progress
However, you can choose to share your achievements:
- ✅ Opt-in sharing: You control what you share and where
- ✅ Certificate sharing: You can display certificates on LinkedIn or portfolios
- ✅ Achievement badges: You decide whether to show accomplishments publicly
🔗 Related Privacy and Security Resources
Learn more about how we protect your information across Mondosol:
Internal Privacy Resources:
External Educational Privacy Resources:
- FERPA Guidelines – U.S. educational privacy law
- Student Privacy Compass – Educational privacy resources
- Future of Privacy Forum – Student privacy advocacy
- Common Sense Privacy Program – Privacy evaluation tools
💡 Best Practices for Protecting Your Learning Data
While we implement robust protections, you can take additional steps to safeguard your learning data:
Secure Your Account
Your account security directly impacts your learning data protection:
- Use a strong, unique password for your Mondosol account
- Enable two-factor authentication for extra security
- Never share your login credentials with others
- Log out from shared or public computers
- Review account activity regularly for suspicious behavior
Be Cautious About Sharing
Think carefully before sharing your learning achievements:
- Consider who can see your shared certificates or badges
- Review privacy settings on social media before posting
- Understand that shared information may be permanent
- Avoid sharing sensitive quiz results or grades publicly
Monitor Your Learning Data
Regularly review your learning records for accuracy:
- Check your progress tracking monthly
- Verify quiz scores and completion records
- Report any discrepancies immediately
- Request corrections for any errors you find
📞 Questions About Learning Data Protection?
If you have specific concerns about how we protect your learning data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Learning Data Privacy Inquiry”
- Response Time: Within 24-48 hours
For urgent privacy concerns:
- Mark your email as “URGENT”
- Include specific details about your concern
- Expect priority response within 4-8 hours
Your educational privacy is our priority. We’re committed to protecting your learning data with the same care we’d want for our own educational records. 📚🔒
Last Updated: October 8, 2025
Leave a Reply
Comprehensive guide to managing your Mondosol privacy settings. Control profile visibility, data sharing, communication preferences, and protect your personal information with granular privacy controls.
Your privacy is in your hands at Mondosol. This comprehensive guide will walk you through every step of managing and customizing your privacy settings to ensure you have complete control over your personal information.
🔒 Privacy Settings Overview
Privacy management is more than just a few toggles—it’s about giving you total control over your digital experience. At Mondosol, we provide granular, easy-to-use privacy controls across multiple dimensions of your account.

Key Privacy Control Areas
You can manage privacy settings in these critical areas:
- Profile Visibility
- Data Sharing Preferences
- Communication Permissions
- Third-Party Integrations
- Content Visibility
- Activity Tracking
🛠️ Accessing Your Privacy Dashboard
To manage your privacy settings, follow these step-by-step instructions:
- Log into your Mondosol account
- Navigate to Settings → Privacy Controls
- Review each section carefully
- Make selections that feel comfortable for you
Pro Tip: Learn more about account security before adjusting settings.
Profile Visibility Options
Control who sees your personal information:
Visibility Levels:
- Public: Anyone can view your profile
- Mondosol Members Only: Visible to registered users
- Private: Completely hidden from other users
- Custom: Create granular visibility rules

Alt text: Multiple privacy levels for controlling profile information visibility
📊 Data Sharing Preferences
Decide exactly how your data is used:
Analytics and Improvement Programs
Choose your level of data contribution:
- Full Participation: Help improve Mondosol’s services
- Limited Sharing: Anonymized data only
- No Participation: Opt-out of all data collection
According to Electronic Frontier Foundation, informed consent is crucial in data sharing.
Third-Party Integration Controls
Manage connections with external services:
Review Connected Apps:
- View all connected applications
- Revoke access for unused or suspicious integrations
- Control what information each app can access
🔔 Communication Permissions
Take control of how and when we communicate:
Email Notification Settings
Customize your communication preferences:
Notification Types:
- Course Updates
- Marketing Communications
- Security Alerts
- Community Notifications
- Promotional Offers
Each category can be individually enabled or disabled.
🌐 International Privacy Compliance
We adhere to global privacy standards:
GDPR and CCPA Compliance
Your rights are protected by:
- Right to access your data
- Right to deletion
- Right to restrict processing
- Right to data portability
Learn more aboutyour data rights.
💡 Privacy Best Practices
Recommendations for maintaining your digital privacy:
- Review settings quarterly
- Use strong, unique passwords
- Enable two-factor authentication
- Be selective about shared information
- Regularly audit connected applications
🚨 Urgent Privacy Concerns?
Contact our privacy team immediately:
- Email: eliomondello@mondosol.com
- Subject: “Privacy Settings Assistance”
- Response Time: Within 24 hours
Your privacy is our priority. 🔐
Internal Resources
Leave a Reply
Discover your comprehensive data privacy rights at Mondosol. Learn how to access, correct, delete, and control your personal information with our transparent privacy framework.
Understanding your data privacy rights is crucial in today’s digital world. At Mondosol, we’re committed to transparency and empowering you with comprehensive control over your personal information.
🛡️ Fundamental Data Privacy Rights
Your rights are not just legal requirements—they’re fundamental protections of your personal information. Here’s a comprehensive breakdown of the rights you have regarding your data.

Core Privacy Rights Framework
You have the following fundamental rights:
- Right to Access: Know what data we collect
- Right to Correction: Update inaccurate information
- Right to Deletion: Request removal of your data
- Right to Restrict Processing: Limit how we use your data
- Right to Data Portability: Receive your data in a usable format
- Right to Object: Oppose certain data processing activities
🔍 Right to Access Your Data
You have the right to know exactly what personal information we collect:
How to Request Your Data
- Email eliomondello@mondosol.com
- Subject: “Data Access Request”
- We’ll provide:
- Complete personal information we hold
- Sources of data collection
- Purpose of data processing
- Retention periods
Learn more aboutcomprehensive data access.

✏️ Right to Correction
Discovered inaccurate information? You can request corrections:
Correction Request Process
- Identify incorrect data
- Provide correct information
- Submit supporting documentation if necessary
- We’ll update your records within 30 days
According to the European Data Protection Board, timely and accurate data is a fundamental privacy right.
🗑️ Right to Deletion (Right to be Forgotten)
You can request complete removal of your personal data:
Deletion Scenarios
- When data is no longer necessary
- If you withdraw consent
- If data was processed unlawfully
- When you object to processing
Important Considerations:
- Some legal records may be retained
- Deletion is permanent and cannot be undone
- You may lose access to services dependent on that data

🛑 Right to Restrict Processing
You can limit how we use your personal data:
Processing Restriction Conditions
- During data accuracy verification
- When processing is unlawful
- When we no longer need the data
- While considering your objection to processing
📦 Right to Data Portability
Receive your data in a structured, machine-readable format:
Portability Features
- Export complete data profile
- Receive data in common formats (JSON, CSV)
- Transfer to another service provider
- Includes:
- Personal information
- Learning data
- Account history
🚫 Right to Object
You can object to certain data processing activities:
Objection Grounds
- Direct marketing
- Automated decision-making
- Processing for research purposes
- Legitimate interest processing
🌐 International Privacy Rights
Our commitment extends beyond regional regulations:
Global Privacy Standards
- GDPR (European Union)
- CCPA (California, USA)
- PIPEDA (Canada)
- APPI (Japan)
Learn more aboutinternational privacy standards.
Internal Resources
📞 Exercise Your Privacy Rights
Questions or want to exercise your rights?
- Email: eliomondello@mondosol.com
- Subject: “Privacy Rights Inquiry”
- Response Time: Within 24-48 hours
Your data, your control. 🔒
Leave a Reply
Discover what privacy regulations Mondosol follows including GDPR, CCPA, UK GDPR, PIPEDA, and international standards. Learn how we protect your data through comprehensive compliance with global privacy laws.
What Privacy Regulations Does Mondosol Follow? ⚖️
Navigating the complex world of privacy regulations can be overwhelming. At Mondosol, we simplify this by adhering to the world’s most stringent privacy standards, ensuring your data receives maximum protection regardless of where you live.
🌍 Global Privacy Compliance Framework
Rather than following minimum requirements, we adopt the highest privacy standards globally. This approach means that all users benefit from comprehensive protection, not just those in specific regions.

Our Compliance Philosophy
We believe privacy is a fundamental right, not a regional privilege. Therefore, we implement:
- Universal high standards for all users
- Proactive compliance with emerging regulations
- Transparent practices across all jurisdictions
- Regular audits to ensure ongoing compliance
🇪🇺 GDPR (General Data Protection Regulation)
The GDPR represents the gold standard in data protection. Implemented in May 2018, this European Union regulation sets comprehensive requirements for personal data handling.
GDPR Core Principles We Follow
Mondosol adheres to all seven GDPR principles:
Lawfulness, Fairness, and Transparency:
- We process data only with valid legal basis
- We inform you clearly about data collection
- We explain how we use your information
- We maintain transparent privacy policies
Purpose Limitation:
- We collect data for specific, explicit purposes
- We don’t repurpose data without your consent
- We document the reason for each data collection
- We limit processing to stated purposes
Data Minimization:
- We collect only necessary information
- We avoid excessive data gathering
- We regularly review what data we truly need
- We delete unnecessary information promptly
Accuracy:
- We maintain accurate and up-to-date records
- We provide tools for you to correct information
- We verify data accuracy regularly
- We update records when you notify us of changes
Storage Limitation:
- We retain data only as long as necessary
- We establish clear retention periods
- We delete data when no longer needed
- We document our retention policies
Integrity and Confidentiality:
- We implement robust security measures
- We encrypt sensitive information
- We protect against unauthorized access
- We train staff on data protection
Accountability:
- We document all processing activities
- We conduct regular compliance audits
- We maintain records of consent
- We report breaches within 72 hours
Learn more about GDPR from the European Commission.

Your GDPR Rights at Mondosol
Under GDPR, you have comprehensive rights:
- Right to Access: Request all data we hold about you
- Right to Rectification: Correct inaccurate information
- Right to Erasure: Request deletion of your data
- Right to Restrict Processing: Limit how we use your data
- Right to Data Portability: Receive your data in portable format
- Right to Object: Oppose certain processing activities
- Rights Related to Automated Decision-Making: Opt out of automated profiling
To exercise these rights, contact eliomondello@mondosol.com.
🇺🇸 CCPA (California Consumer Privacy Act)
The CCPA protects California residents with comprehensive privacy rights. Effective January 2020, this regulation grants significant control over personal information.
CCPA Rights We Honor
California users enjoy these specific rights to:
Know:
- What personal information we collect
- The sources of that information
- The purposes for collection
- Third parties we share with
Delete:
- Request deletion of personal information
- With exceptions for legal obligations
- Confirmed within 45 days
Opt-Out:
- Opt out of data sales (we don’t sell data)
- Control third-party sharing
- Manage marketing preferences
Non-Discrimination:
- Equal service regardless of privacy choices
- No penalties for exercising rights
- Same quality of service for all
Learn more about CCPA from the California Attorney General.
CPRA Enhancement
The California Privacy Rights Act (CPRA), effective January 2023, enhances CCPA with:
- Sensitive personal information protections
- Data minimization requirements
- Purpose limitation enforcement
- Enhanced enforcement mechanisms
We comply fully with both CCPA and CPRA requirements.
🇬🇧 UK GDPR and Data Protection Act 2018
Following Brexit, the UK implemented its own version of GDPR. We maintain compliance with UK-specific requirements:
UK-Specific Compliance
Our UK compliance includes:
- ICO registration and cooperation
- UK data transfer mechanisms
- British standards adherence
- Local representation for UK users
Learn more from the UK Information Commissioner’s Office.
🇨🇦 PIPEDA (Personal Information Protection and Electronic Documents Act)
Canada’s federal privacy law governs private sector data handling. We comply with PIPEDA through:
PIPEDA Compliance Measures
Our Canadian compliance includes:
- Consent requirements for data collection
- Purpose specification before collection
- Limited collection to necessary data
- Accuracy maintenance of records
- Safeguards for personal information
- Openness about privacy practices
- Individual access to personal data
- Challenging compliance mechanisms
Learn more about PIPEDA from the Office of the Privacy Commissioner of Canada.
🌏 APPI (Act on the Protection of Personal Information – Japan)
Japan’s privacy law underwent significant amendments in 2020. We comply with APPI requirements:
APPI Compliance Framework
Our Japanese compliance includes:
- Proper purpose specification
- Lawful acquisition of data
- Accurate maintenance of records
- Security management measures
- Transparent handling of data
- Cross-border transfer safeguards
🇦🇺 Australian Privacy Act
Australia’s Privacy Act governs how organizations handle personal information. We follow the Australian Privacy Principles (APPs):
APP Compliance
Our Australian compliance includes:
- Open and transparent management
- Anonymity and pseudonymity options
- Collection limitations to necessary data
- Use and disclosure restrictions
- Security safeguards implementation
- Access and correction mechanisms
Learn more from the Office of the Australian Information Commissioner.
🌐 Other Regional Privacy Laws
Beyond major regulations, we monitor and comply with emerging privacy laws:
Additional Compliance
We also follow:
- Brazil’s LGPD (Lei Geral de Proteção de Dados)
- South Africa’s POPIA (Protection of Personal Information Act)
- Singapore’s PDPA (Personal Data Protection Act)
- India’s proposed Data Protection Bill
- Various state-level US privacy laws

🏫 Educational Privacy Standards
As an educational platform, we also align with education-specific privacy frameworks:
FERPA Principles
Although FERPA technically applies to US educational institutions receiving federal funding, we adopt its best practices:
- Student consent for educational record disclosure
- Limited access to educational records
- Right to review and correct records
- Annual notification of rights
Learn about FERPA from the US Department of Education.
COPPA Compliance
The Children’s Online Privacy Protection Act protects children under 13. We comply by:
- Not knowingly collecting data from children under 13
- Requiring parental consent for underage users
- Providing parental access to children’s data
- Allowing parents to delete children’s information
Learn about COPPA from the Federal Trade Commission.
🔐 Industry-Specific Security Standards
Beyond privacy regulations, we follow security standards:
ISO 27001
We align with International Organization for Standardization security management:
- Information security management systems
- Risk assessment methodologies
- Security controls implementation
- Continuous improvement processes
SOC 2 Principles
We follow Service Organization Control principles:
- Security: Protection against unauthorized access
- Availability: System availability for operation
- Processing Integrity: Complete and accurate processing
- Confidentiality: Protected confidential information
- Privacy: Personal information collection and use
Learn about SOC 2 from the AICPA.
PCI DSS
For payment processing, we maintain Payment Card Industry Data Security Standard compliance:
- Secure network maintenance
- Cardholder data protection
- Vulnerability management programs
- Access control measures
- Network monitoring and testing
- Information security policies

📋 Compliance Documentation
We maintain comprehensive documentation demonstrating our compliance:
Available Documentation
Upon request, we provide:
- Privacy Impact Assessments (PIAs)
- Data Processing Agreements (DPAs)
- Records of Processing Activities (ROPA)
- Data Transfer Impact Assessments (DTIAs)
- Breach notification procedures
- Compliance audit reports
To request documentation, email eliomondello@mondosol.com with subject “Compliance Documentation Request.”
🔄 Continuous Compliance Monitoring
Privacy regulations constantly evolve. Therefore, we maintain ongoing compliance through:
Our Compliance Process
We ensure continuous compliance by:
- Monitoring regulatory changes globally
- Updating policies and procedures promptly
- Training staff on new requirements
- Conducting regular compliance audits
- Engaging external privacy consultants
- Participating in industry privacy forums
Compliance Team
Our dedicated privacy team:
- Reviews new regulations quarterly
- Assesses impact on our operations
- Implements necessary changes
- Documents compliance measures
- Reports to leadership regularly
🔗 Privacy Regulation Resources
Learn more about privacy regulations and your rights:
Internal Resources:
External Regulatory Resources:
- GDPR Official Portal – European data protection
- California Privacy Rights – CCPA information
- UK ICO – UK data protection authority
- IAPP Resources – International privacy professional association
📞 Privacy Compliance Questions?
If you have questions about our regulatory compliance:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Privacy Regulation Inquiry”
- Response Time: Within 24-48 hours
For specific compliance documentation:
- Subject: “Compliance Documentation Request”
- Include: Specific regulation or document needed
- Delivery: Within 30 days
Your privacy is protected by the world’s strongest regulations, and we’re committed to exceeding every standard. ⚖️🔒
Last Updated: October 8, 2025
Leave a Reply
Learn how to request your personal data from Mondosol. Step-by-step guide to submitting data access requests, understanding your data package, and exercising your privacy rights under GDPR, CCPA, and other regulations.
You have the absolute right to access all personal data we hold about you. At Mondosol, we’ve made the data request process simple, transparent, and efficient. In this comprehensive guide, we’ll walk you through every step of requesting, receiving, and understanding your personal information.
🔍 Understanding Data Access Rights
Your right to access personal data is fundamental under privacy regulations worldwide. This means you can request a complete copy of all information we’ve collected about you.

What Data You Can Request
When you request your data, you’ll receive comprehensive information including:
Personal Account Information:
- Full name and contact details
- Email address and phone number
- Account creation date and history
- Profile information and preferences
- Login credentials (encrypted, not plain text)
Learning and Course Data:
- Course enrollments and completion status
- Quiz results and assessment scores
- Certificates earned and achievements
- Learning progress across all courses
- Time spent on lessons and modules
Communication Records:
- Support tickets and correspondence
- Newsletter subscriptions and preferences
- Email communications we’ve sent
- Feedback and reviews you’ve submitted
Technical and Usage Data:
- Login history with dates and locations
- Device information used to access Mondosol
- IP addresses and browser details
- Activity logs showing platform interactions
Payment and Billing Information:
- Purchase history and transaction records
- Billing addresses and payment methods (last 4 digits only)
- Invoices and receipts for all purchases
- Refund records if applicable
According to privacy experts at the International Association of Privacy Professionals, comprehensive data access is essential for transparency and trust.
📧 How to Submit a Data Request
Requesting your data is straightforward. Follow these simple steps:
Step-by-Step Request Process
Step 1: Compose Your Email
Send your request to: eliomondello@mondosol.com
Subject Line: “Data Access Request”
Email Template:
Subject: Data Access Request
Dear Mondosol Privacy Team,
I am writing to request a complete copy of all personal data you hold about me under [GDPR/CCPA/applicable regulation].
Account Email: [your registered email]
Full Name: [your full name]
Additional Verification: [account creation date or last purchase, if known]
Please provide my data in a commonly used, machine-readable format.
Thank you,
[Your Name]
Step 2: Identity Verification
To protect your privacy, we verify your identity before releasing data:
- We’ll confirm your email address matches our records
- We may ask security questions about your account
- We might request additional verification for sensitive requests
- This process typically takes 1-2 business days
Why verification matters: According to the Federal Trade Commission, proper identity verification prevents unauthorized data access.
Step 3: Processing Time
We process data requests within regulatory timeframes:
- Standard processing: 30 days from verification
- Complex requests: Up to 60 days (we’ll notify you if extension needed)
- Simple requests: Often completed within 7-14 days
- Urgent requests: Contact us to discuss expedited processing

Step 4: Receiving Your Data
Once processed, we’ll deliver your data securely:
Delivery Methods:
- Secure email with encrypted attachment
- Password-protected ZIP file
- Secure download link (expires after 7 days)
- Physical mail upon request (additional processing time)
Data Formats:
- PDF for human-readable documents
- CSV for spreadsheet data
- JSON for machine-readable structured data
- Combined package with all formats
🔐 Security and Privacy During Requests
We take extraordinary measures to protect your data during the request process:
Security Measures
Throughout the process, we ensure:
- Encrypted transmission of all data files
- Secure storage of request documentation
- Access logging for accountability
- Automatic deletion of temporary files after delivery
- Verification protocols to prevent unauthorized access
Learn more about our security practices.
Privacy Protections
We protect your privacy by:
- Never sharing your request with third parties
- Limiting access to authorized privacy team members only
- Documenting all request handling procedures
- Maintaining confidentiality throughout the process

📊 Understanding Your Data Package
When you receive your data, here’s how to interpret it:
Data Package Contents
Your package typically includes:
1. Summary Document (PDF):
- Overview of all data categories
- Explanation of each data type
- Retention periods for different data
- Sources of data collection
2. Detailed Data Files:
- Account_Information.csv: Personal and profile data
- Learning_Records.csv: Course progress and results
- Communication_History.pdf: Email and support records
- Activity_Logs.csv: Login and usage history
- Payment_Records.pdf: Transaction and billing information
3. Metadata and Context:
- Data dictionary explaining field names
- Collection dates for each data point
- Legal basis for processing
- Retention schedules and deletion dates
Reading Your Data Files
Tips for understanding your data:
- Start with the summary document for an overview
- Use spreadsheet software (Excel, Google Sheets) for CSV files
- Check the data dictionary for unfamiliar terms
- Compare dates to understand data collection timeline
- Note retention periods to know when data will be deleted
If you need help interpreting your data, contact eliomondello@mondosol.com.
🔄 What Happens After Your Request
Beyond receiving your data, you have additional options:
Post-Request Actions
After reviewing your data, you can request :
Corrections:
- Identify any inaccurate information
- Submit correction requests with supporting documentation
- We’ll update records within 30 days
- Receive confirmation once corrections are made
Deletion:
- Decide if you want data deleted
- Submit a separate deletion request
- Understand that some data may be retained for legal compliance
- Receive confirmation of deletion within 30 days
Restrictions:
- Limit how we process certain data
- Temporarily suspend processing during disputes
- Maintain data without active use
- Resume processing only with your consent
To export to Another Service:
- Use machine-readable formats for portability
- Transfer data to competitors or other platforms
- Exercise your right to data portability
- Maintain a personal backup of your information
🌍 International Data Requests
Regardless of your location, we honor data access requests:
Region-Specific Considerations
European Union (GDPR):
- 30-day response time (extendable to 60 days)
- Free of charge for reasonable requests
- Machine-readable format provided
- Right to complain to supervisory authority
California (CCPA/CPRA):
- 45-day response time (extendable to 90 days)
- Twice yearly requests allowed
- No discrimination for exercising rights
- Specific categories of data disclosed
United Kingdom (UK GDPR):
- One month response time
- Free access to personal data
- ICO complaint option available
- Same rights as EU GDPR
Canada (PIPEDA):
- 30-day response time
- Reasonable cost may apply for extensive requests
- Privacy Commissioner complaint option
- Access to all personal information
Learn about regional privacy laws from OneTrust DataGuidance.

❓ Common Data Request Questions
Here are answers to frequently asked questions:
FAQ About Data Requests
Q: Is there a fee for requesting my data?
A: No, data requests are completely free for reasonable requests. However, if you make excessive or repetitive requests, we may charge a reasonable administrative fee or refuse the request.
Q: How often can I request my data?
A: You can request your data anytime. However, if you’ve recently received a complete data package, we may ask if you want an updated version rather than a full reprocessing.
Q: Can someone else request my data on my behalf?
A: Yes, with proper authorization. You must provide:
- Written consent authorizing the representative
- Proof of identity for both you and the representative
- Specific scope of what they can access
Q: What if I find errors in my data?
A: Contact us immediately with:
- Specific errors identified
- Correct information with supporting documentation
- We’ll investigate and correct within 30 days
Q: Can I request data for a deleted account?
A: It depends on timing. If your account was recently deleted:
- Within 30 days: We likely still have your data
- After 30 days: Data may be permanently deleted
- Legal retention: Some data kept for 7 years for compliance
Q: Will requesting my data affect my account?
A: No, absolutely not. Requesting your data:
- Doesn’t impact your account status
- Doesn’t affect your access to services
- Doesn’t change your subscription or enrollment
- Is completely confidential
🚨 Urgent Data Access Needs
If you need your data urgently due to legal proceedings or other time-sensitive matters:
Expedited Request Process
Contact us immediately:
- Email: eliomondello@mondosol.com
- Subject: “URGENT: Expedited Data Request”
- Include: Reason for urgency and deadline
We’ll prioritize:
- Legal proceedings: Court orders or subpoenas
- Data breaches: If you suspect unauthorized access
- Account disputes: Billing or service disagreements
- Regulatory investigations: Official inquiries
Expedited processing typically takes 3-7 business days instead of 30 days.
🔗 Related Data Rights Resources
Learn more about your data rights and privacy:
Internal Resources:
External Privacy Resources:
- GDPR Right to Access – European data access rights
- CCPA Data Access – California consumer rights
- Your Data Rights Guide – Comprehensive privacy information
- Data Portability Project – Understanding data portability
📞 Need Help With Your Data Request?
If you have questions about requesting your data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Data Request Assistance”
- Response Time: Within 24-48 hours
For technical issues:
- Subject: “Data Request Technical Support”
- Include: Error messages or specific problems
- Priority response: Within 12-24 hours
For legal or compliance questions:
- Subject: “Data Request Legal Inquiry”
- Include: Specific regulation or legal requirement
- Expert response: Within 48-72 hours
Your data belongs to you. We’re here to help you access it quickly, securely, and completely. 📋🔒
Last Updated: October 8, 2025
Leave a Reply
Educational Privacy (1)
Discover how Mondosol protects your learning data with encryption, access controls, and privacy-focused practices. Learn about your rights to access, correct, and delete your educational records while maintaining complete privacy.
Your learning journey is personal and private. At Mondosol, we understand that your course progress, quiz results, and educational achievements deserve the highest level of protection. In this comprehensive guide, we’ll explain exactly how we safeguard your learning data and ensure your educational privacy.
🔒 Understanding Your Learning Data
Before diving into protection measures, let’s clarify what learning data includes and why protecting it matters.
What Constitutes Learning Data?
Your learning data encompasses all information related to your educational activities on Mondosol:
Course Activity Information:
- Enrollment dates for each course you join
- Progress tracking showing completed lessons and modules
- Time spent on each lesson and course section
- Completion status indicating finished courses
- Certificates earned upon course completion
Assessment and Performance Data:
- Quiz results including scores and answers
- Assignment submissions and instructor feedback
- Test performance across all assessments
- Practice exercise results and attempts
- Skill assessments measuring your proficiency levels
Learning Preferences and Behavior:
- Course interests and topics you explore
- Learning pace preferences (fast-track or standard)
- Study patterns showing when you’re most active
- Content interactions like bookmarks and notes
- Video playback preferences and watch history
According to educational privacy experts at the Student Privacy Compass, protecting learning data is essential for maintaining trust and encouraging honest educational engagement.

🛡️ Multi-Layer Learning Data Protection
Rather than relying on single security measures, we implement multiple protection layers specifically designed for learning data security.
Encryption for Learning Data
First and foremost, we encrypt all your learning data both in transit and at rest:
Data in Transit:
- When you submit quiz answers, we encrypt them using SSL/TLS protocols
- Similarly, course progress updates travel through secure, encrypted channels
- Additionally, all API communications use industry-standard encryption
- Therefore, no one can intercept your learning data during transmission
Data at Rest:
- We encrypt all stored learning data using AES-256 encryption
- Furthermore, we maintain separate encryption keys for different data types
- Moreover, we rotate encryption keys regularly to enhance security
- As a result, your learning records remain unreadable without proper authorization
Research from the National Institute of Standards and Technology emphasizes that encryption is fundamental to protecting sensitive educational records.
Access Control for Educational Records
Not everyone at Mondosol can view your learning data. Instead, we implement strict role-based access controls:
Who Can Access Your Learning Data:
- You: Full access to all your learning records and progress
- Your instructors: Limited access to your performance in their specific courses only
- Support staff: Restricted access only when assisting with technical issues
- System administrators: Encrypted, logged access for maintenance purposes only
Who Cannot Access Your Learning Data:
- ❌ Other students or community members
- ❌ Marketing teams or sales personnel
- ❌ Third-party advertisers or partners
- ❌ Anyone outside Mondosol without your explicit consent
Additionally, we log every instance when someone accesses your learning data, creating a complete audit trail for accountability.

Secure Database Infrastructure
Beyond encryption and access controls, we protect your learning data through robust infrastructure:
Database Security Measures:
- Dedicated servers specifically for educational records
- Firewall protection preventing unauthorized network access
- Regular security audits by independent cybersecurity experts
- Automated backups stored in geographically separate locations
- Disaster recovery systems ensuring data availability
According to database security standards from OWASP, layered security approaches provide the strongest protection for sensitive information.
📊 Learning Data Privacy Practices
Beyond technical security, we implement privacy-focused practices that respect your educational journey.
Data Minimization for Learning Records
We only collect learning data that directly supports your educational experience:
What We Collect and Why:
- Course progress: To show you where you left off and track completion
- Quiz scores: To provide feedback and generate certificates
- Time spent: To optimize course pacing and content length
- Learning preferences: To personalize recommendations
What We Don’t Collect:
- ❌ Unnecessary personal information unrelated to learning
- ❌ Behavioral data for advertising purposes
- ❌ Information about other websites you visit
- ❌ Data from your device beyond what’s needed for platform functionality
Therefore, we minimize your data footprint while maximizing your learning experience.
Anonymized Analytics for Course Improvement
When we analyze learning data to improve courses, we use anonymization techniques:
How We Anonymize Data:
- Remove all personally identifiable information
- Aggregate data across multiple students
- Use statistical methods that prevent re-identification
- Ensure individual students cannot be identified from reports
For example, we might analyze:
- “75% of students complete Module 3 in under 2 hours” ✅
- But never: “John Smith spent 3 hours on Module 3” ❌
Research from the Future of Privacy Forum explains how anonymization protects student privacy while enabling educational improvements.
Instructor Access Limitations
Even your course instructors have limited access to your learning data:
What Instructors Can See:
- ✅ Your progress in their specific course only
- ✅ Your quiz and assignment submissions for grading
- ✅ Your participation in course discussions
- ✅ Your completion status and certificates earned
What Instructors Cannot See:
- ❌ Your activity in other instructors’ courses
- ❌ Your personal contact information (unless you share it)
- ❌ Your payment or billing information
- ❌ Your overall account activity across Mondosol
Furthermore, instructors must agree to strict confidentiality terms before accessing any student data.

🎓 FERPA and Educational Privacy Compliance
As an educational platform, we align our practices with educational privacy regulations, particularly FERPA principles.
FERPA-Aligned Practices
Although FERPA technically applies to U.S. educational institutions receiving federal funding, we adopt its best practices:
FERPA Principles We Follow:
- Student consent: We obtain your permission before sharing learning data
- Limited disclosure: We don’t share educational records without authorization
- Access rights: You can review and request corrections to your learning data
- Security safeguards: We protect educational records from unauthorized access
Learn more about educational privacy rights from the U.S. Department of Education.
International Educational Privacy Standards
Beyond U.S. standards, we comply with international educational privacy requirements:
GDPR Compliance for Learning Data:
- Lawful basis: We process learning data based on contract performance
- Purpose limitation: Data used only for educational purposes
- Data minimization: Collect only necessary learning information
- Storage limitation: Retain data only as long as needed
According to the European Data Protection Board, educational data requires special protection under GDPR.
🔐 Your Control Over Learning Data
You maintain complete control over your learning data throughout your educational journey.
Accessing Your Learning Data
At any time, you can request a complete copy of your learning data:
How to Request Your Learning Data:
- Email eliomondello@mondosol.com
- Subject line: “Learning Data Access Request”
- Include your account email and full name
- Receive your data within 30 days in a readable format
Your data export includes:
- Complete course enrollment history
- All quiz and assessment results
- Certificates and completion records
- Learning preferences and settings
- Progress tracking across all courses
Correcting Learning Data Errors
If you discover inaccuracies in your learning records, you can request corrections:
Common Corrections:
- Quiz scores recorded incorrectly due to technical issues
- Completion status not updating properly
- Certificate information containing errors
- Progress tracking showing incorrect data
To request corrections:
- Contact your course instructor for course-specific issues
- Email support at eliomondello@mondosol.com for technical problems
- Provide specific details about the error
- Receive confirmation once we’ve made corrections
Deleting Your Learning Data
You have the right to request deletion of your learning data:
What Happens When You Delete:
- We remove all your course progress and quiz results
- We delete your certificates and completion records
- We erase your learning preferences and history
- However, we may retain anonymized data for analytics
Important considerations:
- Deletion is permanent and cannot be undone
- You’ll lose all progress and certificates
- You may need to restart courses from the beginning
- Some data may be retained for legal compliance (typically 7 years)
To request deletion:
- Email eliomondello@mondosol.com
- Subject: “Learning Data Deletion Request”
- We’ll process your request within 30 days

Alt text: Student control over learning data including access, correction, and deletion rights
🚫 What We Never Do With Learning Data
To maintain your trust, we make these absolute commitments about your learning data:
We Never Sell Your Learning Data
Unlike some educational platforms, we never sell your learning data to third parties:
- ❌ No data brokers: We don’t sell to data aggregation companies
- ❌ No advertisers: We don’t share learning data for targeted advertising
- ❌ No marketing lists: We don’t sell your information to marketers
- ❌ No third-party analytics: We don’t share identifiable data with external analytics companies
According to a report by the Electronic Frontier Foundation, selling student data undermines educational trust and privacy.
We Never Use Learning Data for Discrimination
Your learning data will never be used against you:
- ❌ Employment decisions: We don’t share data with potential employers without your consent
- ❌ Credit decisions: Learning performance doesn’t affect credit ratings
- ❌ Insurance: Your course activity won’t impact insurance premiums
- ❌ Admissions: We don’t share data with educational institutions without permission
We Never Share Learning Data Publicly
Your educational journey remains private:
- ❌ No public leaderboards: We don’t display your performance publicly without consent
- ❌ No social sharing: We don’t automatically post your progress to social media
- ❌ No public profiles: Your learning data isn’t visible in search engines
- ❌ No community exposure: Other students can’t see your quiz scores or progress
However, you can choose to share your achievements:
- ✅ Opt-in sharing: You control what you share and where
- ✅ Certificate sharing: You can display certificates on LinkedIn or portfolios
- ✅ Achievement badges: You decide whether to show accomplishments publicly
🔗 Related Privacy and Security Resources
Learn more about how we protect your information across Mondosol:
Internal Privacy Resources:
External Educational Privacy Resources:
- FERPA Guidelines – U.S. educational privacy law
- Student Privacy Compass – Educational privacy resources
- Future of Privacy Forum – Student privacy advocacy
- Common Sense Privacy Program – Privacy evaluation tools
💡 Best Practices for Protecting Your Learning Data
While we implement robust protections, you can take additional steps to safeguard your learning data:
Secure Your Account
Your account security directly impacts your learning data protection:
- Use a strong, unique password for your Mondosol account
- Enable two-factor authentication for extra security
- Never share your login credentials with others
- Log out from shared or public computers
- Review account activity regularly for suspicious behavior
Be Cautious About Sharing
Think carefully before sharing your learning achievements:
- Consider who can see your shared certificates or badges
- Review privacy settings on social media before posting
- Understand that shared information may be permanent
- Avoid sharing sensitive quiz results or grades publicly
Monitor Your Learning Data
Regularly review your learning records for accuracy:
- Check your progress tracking monthly
- Verify quiz scores and completion records
- Report any discrepancies immediately
- Request corrections for any errors you find
📞 Questions About Learning Data Protection?
If you have specific concerns about how we protect your learning data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Learning Data Privacy Inquiry”
- Response Time: Within 24-48 hours
For urgent privacy concerns:
- Mark your email as “URGENT”
- Include specific details about your concern
- Expect priority response within 4-8 hours
Your educational privacy is our priority. We’re committed to protecting your learning data with the same care we’d want for our own educational records. 📚🔒
Last Updated: October 8, 2025
Leave a Reply
Student Rights (1)
Discover how Mondosol protects your learning data with encryption, access controls, and privacy-focused practices. Learn about your rights to access, correct, and delete your educational records while maintaining complete privacy.
Your learning journey is personal and private. At Mondosol, we understand that your course progress, quiz results, and educational achievements deserve the highest level of protection. In this comprehensive guide, we’ll explain exactly how we safeguard your learning data and ensure your educational privacy.
🔒 Understanding Your Learning Data
Before diving into protection measures, let’s clarify what learning data includes and why protecting it matters.
What Constitutes Learning Data?
Your learning data encompasses all information related to your educational activities on Mondosol:
Course Activity Information:
- Enrollment dates for each course you join
- Progress tracking showing completed lessons and modules
- Time spent on each lesson and course section
- Completion status indicating finished courses
- Certificates earned upon course completion
Assessment and Performance Data:
- Quiz results including scores and answers
- Assignment submissions and instructor feedback
- Test performance across all assessments
- Practice exercise results and attempts
- Skill assessments measuring your proficiency levels
Learning Preferences and Behavior:
- Course interests and topics you explore
- Learning pace preferences (fast-track or standard)
- Study patterns showing when you’re most active
- Content interactions like bookmarks and notes
- Video playback preferences and watch history
According to educational privacy experts at the Student Privacy Compass, protecting learning data is essential for maintaining trust and encouraging honest educational engagement.

🛡️ Multi-Layer Learning Data Protection
Rather than relying on single security measures, we implement multiple protection layers specifically designed for learning data security.
Encryption for Learning Data
First and foremost, we encrypt all your learning data both in transit and at rest:
Data in Transit:
- When you submit quiz answers, we encrypt them using SSL/TLS protocols
- Similarly, course progress updates travel through secure, encrypted channels
- Additionally, all API communications use industry-standard encryption
- Therefore, no one can intercept your learning data during transmission
Data at Rest:
- We encrypt all stored learning data using AES-256 encryption
- Furthermore, we maintain separate encryption keys for different data types
- Moreover, we rotate encryption keys regularly to enhance security
- As a result, your learning records remain unreadable without proper authorization
Research from the National Institute of Standards and Technology emphasizes that encryption is fundamental to protecting sensitive educational records.
Access Control for Educational Records
Not everyone at Mondosol can view your learning data. Instead, we implement strict role-based access controls:
Who Can Access Your Learning Data:
- You: Full access to all your learning records and progress
- Your instructors: Limited access to your performance in their specific courses only
- Support staff: Restricted access only when assisting with technical issues
- System administrators: Encrypted, logged access for maintenance purposes only
Who Cannot Access Your Learning Data:
- ❌ Other students or community members
- ❌ Marketing teams or sales personnel
- ❌ Third-party advertisers or partners
- ❌ Anyone outside Mondosol without your explicit consent
Additionally, we log every instance when someone accesses your learning data, creating a complete audit trail for accountability.

Secure Database Infrastructure
Beyond encryption and access controls, we protect your learning data through robust infrastructure:
Database Security Measures:
- Dedicated servers specifically for educational records
- Firewall protection preventing unauthorized network access
- Regular security audits by independent cybersecurity experts
- Automated backups stored in geographically separate locations
- Disaster recovery systems ensuring data availability
According to database security standards from OWASP, layered security approaches provide the strongest protection for sensitive information.
📊 Learning Data Privacy Practices
Beyond technical security, we implement privacy-focused practices that respect your educational journey.
Data Minimization for Learning Records
We only collect learning data that directly supports your educational experience:
What We Collect and Why:
- Course progress: To show you where you left off and track completion
- Quiz scores: To provide feedback and generate certificates
- Time spent: To optimize course pacing and content length
- Learning preferences: To personalize recommendations
What We Don’t Collect:
- ❌ Unnecessary personal information unrelated to learning
- ❌ Behavioral data for advertising purposes
- ❌ Information about other websites you visit
- ❌ Data from your device beyond what’s needed for platform functionality
Therefore, we minimize your data footprint while maximizing your learning experience.
Anonymized Analytics for Course Improvement
When we analyze learning data to improve courses, we use anonymization techniques:
How We Anonymize Data:
- Remove all personally identifiable information
- Aggregate data across multiple students
- Use statistical methods that prevent re-identification
- Ensure individual students cannot be identified from reports
For example, we might analyze:
- “75% of students complete Module 3 in under 2 hours” ✅
- But never: “John Smith spent 3 hours on Module 3” ❌
Research from the Future of Privacy Forum explains how anonymization protects student privacy while enabling educational improvements.
Instructor Access Limitations
Even your course instructors have limited access to your learning data:
What Instructors Can See:
- ✅ Your progress in their specific course only
- ✅ Your quiz and assignment submissions for grading
- ✅ Your participation in course discussions
- ✅ Your completion status and certificates earned
What Instructors Cannot See:
- ❌ Your activity in other instructors’ courses
- ❌ Your personal contact information (unless you share it)
- ❌ Your payment or billing information
- ❌ Your overall account activity across Mondosol
Furthermore, instructors must agree to strict confidentiality terms before accessing any student data.

🎓 FERPA and Educational Privacy Compliance
As an educational platform, we align our practices with educational privacy regulations, particularly FERPA principles.
FERPA-Aligned Practices
Although FERPA technically applies to U.S. educational institutions receiving federal funding, we adopt its best practices:
FERPA Principles We Follow:
- Student consent: We obtain your permission before sharing learning data
- Limited disclosure: We don’t share educational records without authorization
- Access rights: You can review and request corrections to your learning data
- Security safeguards: We protect educational records from unauthorized access
Learn more about educational privacy rights from the U.S. Department of Education.
International Educational Privacy Standards
Beyond U.S. standards, we comply with international educational privacy requirements:
GDPR Compliance for Learning Data:
- Lawful basis: We process learning data based on contract performance
- Purpose limitation: Data used only for educational purposes
- Data minimization: Collect only necessary learning information
- Storage limitation: Retain data only as long as needed
According to the European Data Protection Board, educational data requires special protection under GDPR.
🔐 Your Control Over Learning Data
You maintain complete control over your learning data throughout your educational journey.
Accessing Your Learning Data
At any time, you can request a complete copy of your learning data:
How to Request Your Learning Data:
- Email eliomondello@mondosol.com
- Subject line: “Learning Data Access Request”
- Include your account email and full name
- Receive your data within 30 days in a readable format
Your data export includes:
- Complete course enrollment history
- All quiz and assessment results
- Certificates and completion records
- Learning preferences and settings
- Progress tracking across all courses
Correcting Learning Data Errors
If you discover inaccuracies in your learning records, you can request corrections:
Common Corrections:
- Quiz scores recorded incorrectly due to technical issues
- Completion status not updating properly
- Certificate information containing errors
- Progress tracking showing incorrect data
To request corrections:
- Contact your course instructor for course-specific issues
- Email support at eliomondello@mondosol.com for technical problems
- Provide specific details about the error
- Receive confirmation once we’ve made corrections
Deleting Your Learning Data
You have the right to request deletion of your learning data:
What Happens When You Delete:
- We remove all your course progress and quiz results
- We delete your certificates and completion records
- We erase your learning preferences and history
- However, we may retain anonymized data for analytics
Important considerations:
- Deletion is permanent and cannot be undone
- You’ll lose all progress and certificates
- You may need to restart courses from the beginning
- Some data may be retained for legal compliance (typically 7 years)
To request deletion:
- Email eliomondello@mondosol.com
- Subject: “Learning Data Deletion Request”
- We’ll process your request within 30 days

Alt text: Student control over learning data including access, correction, and deletion rights
🚫 What We Never Do With Learning Data
To maintain your trust, we make these absolute commitments about your learning data:
We Never Sell Your Learning Data
Unlike some educational platforms, we never sell your learning data to third parties:
- ❌ No data brokers: We don’t sell to data aggregation companies
- ❌ No advertisers: We don’t share learning data for targeted advertising
- ❌ No marketing lists: We don’t sell your information to marketers
- ❌ No third-party analytics: We don’t share identifiable data with external analytics companies
According to a report by the Electronic Frontier Foundation, selling student data undermines educational trust and privacy.
We Never Use Learning Data for Discrimination
Your learning data will never be used against you:
- ❌ Employment decisions: We don’t share data with potential employers without your consent
- ❌ Credit decisions: Learning performance doesn’t affect credit ratings
- ❌ Insurance: Your course activity won’t impact insurance premiums
- ❌ Admissions: We don’t share data with educational institutions without permission
We Never Share Learning Data Publicly
Your educational journey remains private:
- ❌ No public leaderboards: We don’t display your performance publicly without consent
- ❌ No social sharing: We don’t automatically post your progress to social media
- ❌ No public profiles: Your learning data isn’t visible in search engines
- ❌ No community exposure: Other students can’t see your quiz scores or progress
However, you can choose to share your achievements:
- ✅ Opt-in sharing: You control what you share and where
- ✅ Certificate sharing: You can display certificates on LinkedIn or portfolios
- ✅ Achievement badges: You decide whether to show accomplishments publicly
🔗 Related Privacy and Security Resources
Learn more about how we protect your information across Mondosol:
Internal Privacy Resources:
External Educational Privacy Resources:
- FERPA Guidelines – U.S. educational privacy law
- Student Privacy Compass – Educational privacy resources
- Future of Privacy Forum – Student privacy advocacy
- Common Sense Privacy Program – Privacy evaluation tools
💡 Best Practices for Protecting Your Learning Data
While we implement robust protections, you can take additional steps to safeguard your learning data:
Secure Your Account
Your account security directly impacts your learning data protection:
- Use a strong, unique password for your Mondosol account
- Enable two-factor authentication for extra security
- Never share your login credentials with others
- Log out from shared or public computers
- Review account activity regularly for suspicious behavior
Be Cautious About Sharing
Think carefully before sharing your learning achievements:
- Consider who can see your shared certificates or badges
- Review privacy settings on social media before posting
- Understand that shared information may be permanent
- Avoid sharing sensitive quiz results or grades publicly
Monitor Your Learning Data
Regularly review your learning records for accuracy:
- Check your progress tracking monthly
- Verify quiz scores and completion records
- Report any discrepancies immediately
- Request corrections for any errors you find
📞 Questions About Learning Data Protection?
If you have specific concerns about how we protect your learning data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Learning Data Privacy Inquiry”
- Response Time: Within 24-48 hours
For urgent privacy concerns:
- Mark your email as “URGENT”
- Include specific details about your concern
- Expect priority response within 4-8 hours
Your educational privacy is our priority. We’re committed to protecting your learning data with the same care we’d want for our own educational records. 📚🔒
Last Updated: October 8, 2025
Leave a Reply
Transparency (2)
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Transparency is the foundation of trust. We believe you have the right to know exactly what information we collect, why we collect it, and how we use it. Here’s a complete breakdown of the personal data Mondosol collects.
👤 Account Information
When you create a Mondosol account, we collect:
Required Information
- Full Name: To personalize your experience and address you properly
- Email Address: For account verification, login, and important communications
- Username: Your unique identifier on the platform
- Password: Encrypted and never stored in plain text
Optional Information
- Profile Picture: To personalize your learning profile
- Bio/Description: To share information with the community
- Location/Country: To provide localized content and comply with regional regulations
- Language Preferences: To deliver content in your preferred language(s)
Why We Collect This: To create and manage your account, verify your identity, and provide personalized services.
📚 Learning & Course Data
To track your progress and improve your learning experience:
Course Activity
- Enrollment Dates: When you start each course
- Progress Tracking: Lessons completed, modules finished
- Time Spent: Duration on each lesson and course
- Completion Status: Courses finished and certificates earned
Assessment Data
- Quiz Results: Scores and answers (for feedback and improvement)
- Assignment Submissions: Your work and instructor feedback
- Test Performance: Assessment results and analytics
Learning Preferences
- Course Interests: Topics you’re interested in
- Learning Goals: Your stated objectives
- Skill Levels: Self-reported or assessed proficiency
- Preferred Learning Pace: Fast-track or standard progression
Why We Collect This: To track your progress, provide certificates, personalize recommendations, and improve course content.
💳 Payment & Billing Information
When you make a purchase:
Billing Details
- Billing Name: Name on payment method
- Billing Address: Required for payment processing
- Country/Region: For tax calculations and compliance
- VAT/Tax ID: If applicable for business purchases
Payment Information
- Payment Method Type: Credit card, PayPal, etc.
- Last 4 Digits: For payment method identification
- Transaction History: Purchase dates, amounts, and order details
Important: We never store complete credit card numbers. All payment processing is handled by certified third-party processors (Stripe, PayPal) that are PCI DSS compliant.
Why We Collect This: To process payments, issue invoices, handle refunds, and comply with financial regulations.
💻 Technical & Usage Data
To improve platform performance and user experience:
Device Information
- IP Address: For security, fraud prevention, and geographic content delivery
- Browser Type & Version: To ensure compatibility
- Operating System: To optimize platform performance
- Device Type: Desktop, mobile, or tablet for responsive design
Usage Analytics
- Pages Visited: Which pages you view and how often
- Click Patterns: What buttons and links you interact with
- Session Duration: How long you spend on the platform
- Referral Source: How you found Mondosol (search, social media, direct)
Cookies & Tracking
- Essential Cookies: Required for platform functionality
- Analytics Cookies: To understand user behavior (you can opt-out)
- Marketing Cookies: For personalized advertising (you can opt-out)
Why We Collect This: To improve platform performance, fix bugs, understand user behavior, and enhance user experience.
📧 Communication Data
When you interact with us:
Email Communications
- Support Tickets: Your questions and our responses
- Newsletter Subscriptions: Topics you’re interested in
- Marketing Preferences: What communications you want to receive
- Unsubscribe Requests: Your opt-out preferences
Community Interactions
- Comments & Reviews: Your feedback on courses
- Forum Posts: Community discussions and contributions
- Messages: Direct communications with instructors or support
Why We Collect This: To provide customer support, send requested information, and facilitate community interaction.
🤝 Social Media & Third-Party Data
If you connect social accounts or use third-party services:
- Social Profile Information: Name, profile picture, email (if you sign up via Facebook, Google, LinkedIn)
- Third-Party Integrations: Data from connected apps (with your permission)
- Affiliate Tracking: If you arrive through an affiliate link
Why We Collect This: To simplify account creation, enable social sharing, and track affiliate referrals.
🚫 What We DON’T Collect
We respect your privacy and never collect:
- ❌ Sensitive personal data (race, religion, political views, health information)
- ❌ Data from children under 13 without parental consent
- ❌ Information from your device without permission
- ❌ Data unrelated to our services
- ❌ Information we don’t need for legitimate purposes
📊 How Long We Keep Your Data
We follow data minimization principles:
- Active Accounts: Data retained while your account is active
- Inactive Accounts: Deleted after 3 years of inactivity (with prior notice)
- Legal Requirements: Some data retained longer for legal/tax compliance (typically 7 years)
- Marketing Data: Removed immediately upon unsubscribe
- Right to Erasure: You can request deletion anytime
🔒 Your Data Rights
You have complete control over your data:
- Access: Request a copy of all data we hold
- Correction: Update inaccurate information
- Deletion: Request complete data removal
- Portability: Receive your data in machine-readable format
- Objection: Opt-out of certain data processing
Learn more about your data rights →
🔗 Related Resources
Privacy & Security:
External Resources:
- GDPR Data Collection Guidelines – European standards
- CCPA Consumer Rights – California privacy law
- ICO Data Protection Guide – UK regulations
📞 Questions About Your Data?
We’re committed to transparency. If you have questions about what data we collect:
- Email: eliomondello@mondosol.com
- Subject: “Data Collection Inquiry”
- Response Time: Within 24 hours
We collect only what we need, protect what we collect, and respect your choices. 🔒
Last Updated: October 8, 2025
Leave a Reply
Complete transparency on what personal data Mondosol collects. Learn about account information, learning data, payment details, technical data, and your rights to access, correct, or delete your information.
Your personal information deserves the highest level of protection. At Mondosol, we implement comprehensive security measures to ensure your data remains safe, private, and secure at all times. In this guide, we’ll walk you through every layer of protection we’ve built to safeguard your information.
🛡️ Our Multi-Layer Security Approach
Rather than relying on just one security measure, we use multiple layers of protection to safeguard your personal information. As a result, your data benefits from redundant security systems that work together seamlessly.
SSL/TLS Encryption
First and foremost, we encrypt all data transmitted between your device and our servers using industry-standard SSL/TLS protocols. Consequently, your information becomes scrambled during transmission, making it unreadable to unauthorized parties.
In practice, this means:
- When you log in, your password travels encrypted through the internet
- Similarly, when you submit course work, the content remains protected
- Additionally, all payment information transfers through secure channels
- Therefore, hackers cannot intercept your data even if they access the network
To verify this protection, always look for the padlock icon in your browser’s address bar when using Mondosol. Furthermore, you can click the padlock to view our security certificate details.
Secure Server Infrastructure
Beyond encryption in transit, we also protect your data at rest. Specifically, we store your personal data on secure servers with restricted physical and digital access.
To accomplish this, we implement several protective measures:
- State-of-the-art firewalls protect against unauthorized intrusion attempts
- In addition, our 24/7 server monitoring detects and responds to potential threats in real-time
- Moreover, we maintain physical security at our data centers with biometric access controls
- As an extra precaution, we conduct regular security perimeter assessments
As a result of these measures, your data remains protected even when you’re not actively using the platform.
Data Encryption at Rest
Not only do we encrypt data during transmission, but also when we store it on our servers. In other words, your sensitive information stays encrypted whether it’s moving or sitting in our database.
To enhance this protection further, we implement additional safeguards:
- First, we manage encryption keys separately from the data itself
- Second, we rotate encryption keys regularly to minimize risk
- Third, we require multi-factor authentication for all system access
- Finally, we maintain encrypted backups in geographically separate locations
Therefore, even in the unlikely event of a server breach, your data remains unreadable without the encryption keys.
🔍 Regular Security Audits & Testing
Rather than waiting for problems to occur, we proactively identify and address vulnerabilities through comprehensive testing programs.
Quarterly Security Assessments
Every three months, independent security experts thoroughly review our systems. During these assessments, they:
- First, examine our infrastructure for potential weaknesses
- Then, test our security protocols against current threat models
- Subsequently, provide detailed recommendations for improvements
- Finally, verify that we’ve implemented previous recommendations
As a result, we stay ahead of emerging security threats and maintain industry-leading protection standards.
Penetration Testing
In addition to audits, we conduct regular penetration testing. Essentially, this means we hire ethical hackers to attempt breaking into our systems. Through this process, we:
- Initially, simulate real-world attack scenarios
- Next, identify vulnerabilities before malicious actors can exploit them
- Then, patch any discovered weaknesses immediately
- Ultimately, strengthen our defenses based on test results
Consequently, our security improves continuously through controlled testing.
Vulnerability Scanning
Beyond manual testing, automated tools continuously monitor for security gaps. Specifically, these systems:
- Constantly scan for known vulnerabilities in our software
- Immediately alert our security team when they detect potential issues
- Subsequently, trigger automatic patching for critical vulnerabilities
- Finally, generate reports for our security review process
Therefore, we can respond to new threats within hours rather than days or weeks.
Code Reviews
Before deploying any updates, our team conducts security-focused code reviews. During this process, we:
- First, examine all new code for security vulnerabilities
- Then, verify compliance with security best practices
- Additionally, test for common attack vectors like SQL injection
- Finally, require approval from multiple security team members
As a result, we prevent security issues from reaching our production environment.
📊 Data Minimization Principle
Unlike many platforms that collect excessive information, we only collect what we truly need. In fact, this principle guides every data collection decision we make.
Purpose Limitation
Specifically, we collect data only for specific, legitimate purposes. For example:
- When you create an account, we collect your email for login and communication
- Similarly, when you enroll in a course, we track your progress for certification
- However, we never collect data “just in case” we might need it later
- Instead, every data point serves a clear, documented purpose
Therefore, we minimize the amount of personal information at risk.
Storage Limitation
Furthermore, we retain information only as long as necessary. In practice, this means:
- Active account data remains available while you use our services
- However, after three years of inactivity, we send deletion notices
- Subsequently, we remove inactive account data unless you respond
- Additionally, we delete temporary data like session tokens immediately after use
As a result, we don’t accumulate unnecessary personal information over time.
Regular Data Purging
In addition to automated deletion, we conduct regular data purging reviews. During these reviews, we:
- First, identify outdated or unnecessary information
- Then, verify that legal retention requirements don’t apply
- Next, securely delete the identified data using military-grade methods
- Finally, document the deletion for compliance purposes
Consequently, your data footprint remains minimal and manageable.
No Excessive Collection
Most importantly, we never ask for information we don’t need. For instance:
- We don’t request your social security number or national ID
- Similarly, we don’t collect sensitive data about race, religion, or health
- Instead, we limit collection to essential account and learning information
- Therefore, you share only what’s necessary for your educational experience
As a result, you maintain greater privacy and control over your personal information.
👥 Strict Access Controls
Not everyone can access your data. In fact, we implement rigorous access controls to ensure only authorized personnel can view your information.
Role-Based Access
First and foremost, team members access only the data necessary for their specific role. For example:
- Customer support can view account details but not payment information
- Meanwhile, instructors see only their students’ course progress
- Similarly, developers access anonymized test data, not production information
- In contrast, only senior security personnel can access full system logs
Therefore, we minimize the number of people who can view your complete profile.
Authentication Protocols
Beyond role restrictions, we implement multi-factor authentication for all system access. Specifically, this means:
- First, employees must enter their password
- Then, they must provide a second factor (authenticator app or hardware token)
- Additionally, they must access systems from approved devices only
- Furthermore, suspicious login attempts trigger immediate security reviews
As a result, unauthorized individuals cannot access our systems even if they steal a password.
Activity Logging
To ensure accountability, we log and monitor all data access. In practice, this means:
- Every time someone views your data, we record who, when, and why
- Subsequently, security systems analyze these logs for unusual patterns
- If suspicious activity occurs, automated alerts notify our security team immediately
- Finally, we retain these logs for audit and compliance purposes
Consequently, we can detect and investigate any unauthorized access attempts.
Background Checks
Before hiring, all employees undergo comprehensive security clearance checks. This process includes:
- First, criminal background verification
- Then, employment history validation
- Additionally, reference checks from previous employers
- Finally, security training and confidentiality agreement signing
Therefore, we ensure that only trustworthy individuals handle your data.
Confidentiality Agreements
In addition to background checks, legal obligations ensure we protect your privacy. Specifically:
- All employees sign comprehensive confidentiality agreements
- These agreements legally bind them to protect user data
- Furthermore, violations result in immediate termination and legal action
- Moreover, these obligations continue even after employment ends
As a result, your data remains protected by both technical and legal safeguards.
💾 Secure Backup Systems
To protect against data loss, we maintain robust backup systems. However, these backups receive the same security protection as your live data.
Encrypted Backups
First and foremost, we fully encrypt all backups using the same standards as production data. This means:
- Even if someone steals backup media, they cannot read the data
- Additionally, we use separate encryption keys for backups and production
- Furthermore, we rotate backup encryption keys on a regular schedule
- Therefore, your historical data remains as secure as your current information
Geographic Redundancy
Beyond encryption, we store backups in multiple secure locations. Specifically:
- Primary backups reside in our main data center
- Secondary backups exist in a geographically separate facility
- Additionally, we maintain offline backups for disaster recovery
- Moreover, all backup locations meet the same security standards
As a result, your data survives even catastrophic events like natural disasters.
Regular Testing
Unlike many organizations, we don’t just create backups—we test them. In fact, we test backup restoration procedures monthly to verify effectiveness. During these tests, we:
- First, select random backup files for restoration
- Then, restore them to a test environment
- Next, verify data integrity and completeness
- Finally, document any issues and implement improvements
Consequently, we know our backups will work when we need them.
Disaster Recovery Plan
In addition to backups, we maintain a comprehensive disaster recovery plan. This plan ensures:
- First, we can restore services within hours of any incident
- Second, your data remains accessible even during emergencies
- Third, we maintain business continuity during disasters
- Finally, we communicate clearly with users during any service interruptions
Therefore, you can trust that your learning progress and data remain safe.
🔐 Payment Security
Because financial information requires special protection, we implement additional security measures for all payment processing.
PCI DSS Compliance
First and foremost, we follow Payment Card Industry Data Security Standards (PCI DSS). In practice, this means:
- We undergo annual security assessments by certified auditors
- Additionally, we maintain network segmentation to isolate payment systems
- Furthermore, we implement strict access controls for payment data
- Moreover, we conduct quarterly network vulnerability scans
As a result, your payment information receives bank-level security protection.
Third-Party Processors
Rather than handling payments directly, we process all transactions through certified secure providers like Stripe and PayPal. This approach offers several advantages:
- First, these processors specialize in payment security
- Second, they maintain PCI DSS Level 1 certification (the highest standard)
- Additionally, they handle fraud detection and prevention
- Furthermore, they assume liability for payment security
Therefore, your financial information benefits from industry-leading protection.
No Card Storage
Most importantly, we never store complete credit card numbers. Instead:
- Payment processors store your card details securely
- We receive only the last four digits for display purposes
- Additionally, we never see or store CVV security codes
- Furthermore, we cannot access your full payment information
Consequently, even if someone breaches our systems, they cannot steal your credit card data.
Tokenization
In addition to not storing cards, we replace payment information with secure tokens. Essentially, this means:
- When you save a payment method, we receive a random token
- This token references your card without containing actual card data
- Subsequently, we use this token for future transactions
- However, the token is useless to anyone except our payment processor
Therefore, your payment information remains protected through multiple security layers.
📱 Additional Security Measures
Beyond the core protections, we implement several additional security measures to safeguard your data.
GDPR Compliance
First, we maintain full compliance with EU General Data Protection Regulation (GDPR). This means:
- We respect all your data rights (access, deletion, portability)
- Additionally, we obtain clear consent before collecting data
- Furthermore, we process data lawfully and transparently
- Moreover, we report any breaches within 72 hours
Therefore, you benefit from Europe’s strongest privacy protections regardless of your location.
Privacy by Design
Rather than adding security later, we build it into every feature from the ground up. In practice, this means:
- When designing new features, we consider privacy implications first
- Subsequently, we implement privacy-protective defaults
- Additionally, we minimize data collection in all new features
- Finally, we conduct privacy impact assessments before launch
As a result, security and privacy are fundamental to our platform, not afterthoughts.
Incident Response Plan
In case of security incidents, we maintain rapid response procedures. Our plan includes:
- Immediate containment protocols to limit damage
- Subsequently, forensic investigation to understand the scope
- Then, user notification within required timeframes
- Finally, remediation and prevention of future incidents
Therefore, we can respond quickly and effectively to any security event.
User Education
Because security is a partnership, we provide resources to help you protect your own account. These resources include:
- Security best practices guides and tutorials
- Regular updates about emerging threats
- Additionally, tips for creating strong passwords
- Furthermore, guidance on recognizing phishing attempts
Consequently, you can take an active role in protecting your account.
Regular Updates
Finally, we keep our systems and software current with security patches. Specifically:
- We monitor security bulletins from all our software vendors
- Then, we test patches in our development environment
- Subsequently, we deploy critical patches within 24-48 hours
- Additionally, we conduct regular system updates during maintenance windows
As a result, we protect against newly discovered vulnerabilities quickly.
🚨 What We Do in Case of a Breach
In the unlikely event of a security breach, we take immediate and comprehensive action to protect you.
Immediate Containment
First and foremost, we isolate the threat within minutes of detection. This involves:
- Immediately, our automated systems detect unusual activity
- Then, they trigger containment protocols automatically
- Subsequently, our security team assesses the situation
- Finally, we implement additional manual containment measures
Therefore, we minimize the potential impact of any security incident.
Investigation
Once contained, we conduct thorough forensic analysis to understand the scope. During this investigation, we:
- First, determine what data the attackers accessed
- Then, identify how they gained access
- Next, assess the extent of the compromise
- Finally, document all findings for regulatory reporting
Consequently, we understand exactly what happened and can respond appropriately.
User Notification
In accordance with GDPR, we notify affected users within 72 hours. Our notification includes:
- First, a clear explanation of what happened
- Then, details about what data was affected
- Additionally, steps we’re taking to address the issue
- Furthermore, recommendations for protecting yourself
- Finally, contact information for questions and support
Therefore, you receive timely and transparent communication about any incidents affecting your data.
Remediation
After notification, we patch vulnerabilities immediately. This process includes:
- First, fixing the specific vulnerability that was exploited
- Then, conducting a comprehensive security review
- Subsequently, implementing additional protective measures
- Finally, retesting to ensure the issue is fully resolved
As a result, we prevent similar incidents from occurring in the future.
Transparency
Throughout the process, we ensure full disclosure of what happened and our response. Specifically, we:
- Publish detailed incident reports on our website
- Additionally, update users regularly as we learn more
- Furthermore, share lessons learned with the security community
- Moreover, implement recommended improvements from external experts
Therefore, we maintain accountability and continuously improve our security posture.
🔗 Related Resources
To learn more about your security and privacy, explore these helpful resources:
Last Updated: October 8, 2025
Leave a Reply
User Rights (2)
Discover your comprehensive data privacy rights at Mondosol. Learn how to access, correct, delete, and control your personal information with our transparent privacy framework.
Understanding your data privacy rights is crucial in today’s digital world. At Mondosol, we’re committed to transparency and empowering you with comprehensive control over your personal information.
🛡️ Fundamental Data Privacy Rights
Your rights are not just legal requirements—they’re fundamental protections of your personal information. Here’s a comprehensive breakdown of the rights you have regarding your data.

Core Privacy Rights Framework
You have the following fundamental rights:
- Right to Access: Know what data we collect
- Right to Correction: Update inaccurate information
- Right to Deletion: Request removal of your data
- Right to Restrict Processing: Limit how we use your data
- Right to Data Portability: Receive your data in a usable format
- Right to Object: Oppose certain data processing activities
🔍 Right to Access Your Data
You have the right to know exactly what personal information we collect:
How to Request Your Data
- Email eliomondello@mondosol.com
- Subject: “Data Access Request”
- We’ll provide:
- Complete personal information we hold
- Sources of data collection
- Purpose of data processing
- Retention periods
Learn more aboutcomprehensive data access.

✏️ Right to Correction
Discovered inaccurate information? You can request corrections:
Correction Request Process
- Identify incorrect data
- Provide correct information
- Submit supporting documentation if necessary
- We’ll update your records within 30 days
According to the European Data Protection Board, timely and accurate data is a fundamental privacy right.
🗑️ Right to Deletion (Right to be Forgotten)
You can request complete removal of your personal data:
Deletion Scenarios
- When data is no longer necessary
- If you withdraw consent
- If data was processed unlawfully
- When you object to processing
Important Considerations:
- Some legal records may be retained
- Deletion is permanent and cannot be undone
- You may lose access to services dependent on that data

🛑 Right to Restrict Processing
You can limit how we use your personal data:
Processing Restriction Conditions
- During data accuracy verification
- When processing is unlawful
- When we no longer need the data
- While considering your objection to processing
📦 Right to Data Portability
Receive your data in a structured, machine-readable format:
Portability Features
- Export complete data profile
- Receive data in common formats (JSON, CSV)
- Transfer to another service provider
- Includes:
- Personal information
- Learning data
- Account history
🚫 Right to Object
You can object to certain data processing activities:
Objection Grounds
- Direct marketing
- Automated decision-making
- Processing for research purposes
- Legitimate interest processing
🌐 International Privacy Rights
Our commitment extends beyond regional regulations:
Global Privacy Standards
- GDPR (European Union)
- CCPA (California, USA)
- PIPEDA (Canada)
- APPI (Japan)
Learn more aboutinternational privacy standards.
Internal Resources
📞 Exercise Your Privacy Rights
Questions or want to exercise your rights?
- Email: eliomondello@mondosol.com
- Subject: “Privacy Rights Inquiry”
- Response Time: Within 24-48 hours
Your data, your control. 🔒
Leave a Reply
Learn how to request your personal data from Mondosol. Step-by-step guide to submitting data access requests, understanding your data package, and exercising your privacy rights under GDPR, CCPA, and other regulations.
You have the absolute right to access all personal data we hold about you. At Mondosol, we’ve made the data request process simple, transparent, and efficient. In this comprehensive guide, we’ll walk you through every step of requesting, receiving, and understanding your personal information.
🔍 Understanding Data Access Rights
Your right to access personal data is fundamental under privacy regulations worldwide. This means you can request a complete copy of all information we’ve collected about you.

What Data You Can Request
When you request your data, you’ll receive comprehensive information including:
Personal Account Information:
- Full name and contact details
- Email address and phone number
- Account creation date and history
- Profile information and preferences
- Login credentials (encrypted, not plain text)
Learning and Course Data:
- Course enrollments and completion status
- Quiz results and assessment scores
- Certificates earned and achievements
- Learning progress across all courses
- Time spent on lessons and modules
Communication Records:
- Support tickets and correspondence
- Newsletter subscriptions and preferences
- Email communications we’ve sent
- Feedback and reviews you’ve submitted
Technical and Usage Data:
- Login history with dates and locations
- Device information used to access Mondosol
- IP addresses and browser details
- Activity logs showing platform interactions
Payment and Billing Information:
- Purchase history and transaction records
- Billing addresses and payment methods (last 4 digits only)
- Invoices and receipts for all purchases
- Refund records if applicable
According to privacy experts at the International Association of Privacy Professionals, comprehensive data access is essential for transparency and trust.
📧 How to Submit a Data Request
Requesting your data is straightforward. Follow these simple steps:
Step-by-Step Request Process
Step 1: Compose Your Email
Send your request to: eliomondello@mondosol.com
Subject Line: “Data Access Request”
Email Template:
Subject: Data Access Request
Dear Mondosol Privacy Team,
I am writing to request a complete copy of all personal data you hold about me under [GDPR/CCPA/applicable regulation].
Account Email: [your registered email]
Full Name: [your full name]
Additional Verification: [account creation date or last purchase, if known]
Please provide my data in a commonly used, machine-readable format.
Thank you,
[Your Name]
Step 2: Identity Verification
To protect your privacy, we verify your identity before releasing data:
- We’ll confirm your email address matches our records
- We may ask security questions about your account
- We might request additional verification for sensitive requests
- This process typically takes 1-2 business days
Why verification matters: According to the Federal Trade Commission, proper identity verification prevents unauthorized data access.
Step 3: Processing Time
We process data requests within regulatory timeframes:
- Standard processing: 30 days from verification
- Complex requests: Up to 60 days (we’ll notify you if extension needed)
- Simple requests: Often completed within 7-14 days
- Urgent requests: Contact us to discuss expedited processing

Step 4: Receiving Your Data
Once processed, we’ll deliver your data securely:
Delivery Methods:
- Secure email with encrypted attachment
- Password-protected ZIP file
- Secure download link (expires after 7 days)
- Physical mail upon request (additional processing time)
Data Formats:
- PDF for human-readable documents
- CSV for spreadsheet data
- JSON for machine-readable structured data
- Combined package with all formats
🔐 Security and Privacy During Requests
We take extraordinary measures to protect your data during the request process:
Security Measures
Throughout the process, we ensure:
- Encrypted transmission of all data files
- Secure storage of request documentation
- Access logging for accountability
- Automatic deletion of temporary files after delivery
- Verification protocols to prevent unauthorized access
Learn more about our security practices.
Privacy Protections
We protect your privacy by:
- Never sharing your request with third parties
- Limiting access to authorized privacy team members only
- Documenting all request handling procedures
- Maintaining confidentiality throughout the process

📊 Understanding Your Data Package
When you receive your data, here’s how to interpret it:
Data Package Contents
Your package typically includes:
1. Summary Document (PDF):
- Overview of all data categories
- Explanation of each data type
- Retention periods for different data
- Sources of data collection
2. Detailed Data Files:
- Account_Information.csv: Personal and profile data
- Learning_Records.csv: Course progress and results
- Communication_History.pdf: Email and support records
- Activity_Logs.csv: Login and usage history
- Payment_Records.pdf: Transaction and billing information
3. Metadata and Context:
- Data dictionary explaining field names
- Collection dates for each data point
- Legal basis for processing
- Retention schedules and deletion dates
Reading Your Data Files
Tips for understanding your data:
- Start with the summary document for an overview
- Use spreadsheet software (Excel, Google Sheets) for CSV files
- Check the data dictionary for unfamiliar terms
- Compare dates to understand data collection timeline
- Note retention periods to know when data will be deleted
If you need help interpreting your data, contact eliomondello@mondosol.com.
🔄 What Happens After Your Request
Beyond receiving your data, you have additional options:
Post-Request Actions
After reviewing your data, you can request :
Corrections:
- Identify any inaccurate information
- Submit correction requests with supporting documentation
- We’ll update records within 30 days
- Receive confirmation once corrections are made
Deletion:
- Decide if you want data deleted
- Submit a separate deletion request
- Understand that some data may be retained for legal compliance
- Receive confirmation of deletion within 30 days
Restrictions:
- Limit how we process certain data
- Temporarily suspend processing during disputes
- Maintain data without active use
- Resume processing only with your consent
To export to Another Service:
- Use machine-readable formats for portability
- Transfer data to competitors or other platforms
- Exercise your right to data portability
- Maintain a personal backup of your information
🌍 International Data Requests
Regardless of your location, we honor data access requests:
Region-Specific Considerations
European Union (GDPR):
- 30-day response time (extendable to 60 days)
- Free of charge for reasonable requests
- Machine-readable format provided
- Right to complain to supervisory authority
California (CCPA/CPRA):
- 45-day response time (extendable to 90 days)
- Twice yearly requests allowed
- No discrimination for exercising rights
- Specific categories of data disclosed
United Kingdom (UK GDPR):
- One month response time
- Free access to personal data
- ICO complaint option available
- Same rights as EU GDPR
Canada (PIPEDA):
- 30-day response time
- Reasonable cost may apply for extensive requests
- Privacy Commissioner complaint option
- Access to all personal information
Learn about regional privacy laws from OneTrust DataGuidance.

❓ Common Data Request Questions
Here are answers to frequently asked questions:
FAQ About Data Requests
Q: Is there a fee for requesting my data?
A: No, data requests are completely free for reasonable requests. However, if you make excessive or repetitive requests, we may charge a reasonable administrative fee or refuse the request.
Q: How often can I request my data?
A: You can request your data anytime. However, if you’ve recently received a complete data package, we may ask if you want an updated version rather than a full reprocessing.
Q: Can someone else request my data on my behalf?
A: Yes, with proper authorization. You must provide:
- Written consent authorizing the representative
- Proof of identity for both you and the representative
- Specific scope of what they can access
Q: What if I find errors in my data?
A: Contact us immediately with:
- Specific errors identified
- Correct information with supporting documentation
- We’ll investigate and correct within 30 days
Q: Can I request data for a deleted account?
A: It depends on timing. If your account was recently deleted:
- Within 30 days: We likely still have your data
- After 30 days: Data may be permanently deleted
- Legal retention: Some data kept for 7 years for compliance
Q: Will requesting my data affect my account?
A: No, absolutely not. Requesting your data:
- Doesn’t impact your account status
- Doesn’t affect your access to services
- Doesn’t change your subscription or enrollment
- Is completely confidential
🚨 Urgent Data Access Needs
If you need your data urgently due to legal proceedings or other time-sensitive matters:
Expedited Request Process
Contact us immediately:
- Email: eliomondello@mondosol.com
- Subject: “URGENT: Expedited Data Request”
- Include: Reason for urgency and deadline
We’ll prioritize:
- Legal proceedings: Court orders or subpoenas
- Data breaches: If you suspect unauthorized access
- Account disputes: Billing or service disagreements
- Regulatory investigations: Official inquiries
Expedited processing typically takes 3-7 business days instead of 30 days.
🔗 Related Data Rights Resources
Learn more about your data rights and privacy:
Internal Resources:
External Privacy Resources:
- GDPR Right to Access – European data access rights
- CCPA Data Access – California consumer rights
- Your Data Rights Guide – Comprehensive privacy information
- Data Portability Project – Understanding data portability
📞 Need Help With Your Data Request?
If you have questions about requesting your data:
Contact Our Privacy Team:
- Email: eliomondello@mondosol.com
- Subject: “Data Request Assistance”
- Response Time: Within 24-48 hours
For technical issues:
- Subject: “Data Request Technical Support”
- Include: Error messages or specific problems
- Priority response: Within 12-24 hours
For legal or compliance questions:
- Subject: “Data Request Legal Inquiry”
- Include: Specific regulation or legal requirement
- Expert response: Within 48-72 hours
Your data belongs to you. We’re here to help you access it quickly, securely, and completely. 📋🔒
Last Updated: October 8, 2025
Leave a Reply